.avif)
DFIR
The 2024-25 financial year saw a large rise in the number and scale of cyber incidents affecting Australian and New Zealand organisations. The Triskele Labs Digital Forensics and Incident Response (DFIR) team responded to 201 incidents that impacted small, medium and enterprise organisations across the region.

Executive Summary
The 2024-25 financial year saw a large rise in the number and scale of cyber incidents affecting Australian and New Zealand organisations. The Triskele Labs Digital Forensics and Incident Response (DFIR) team responded to 201 incidents that impacted small, medium and enterprise organisations across the region.
This year’s report, once again, provides real statistics from incidents responded to, helping organisations understand how to protect themselves.
BEC and Ransomware Dominate the Threat Landscape
Across industries and geographies, the majority of incidents stemmed from Business Email Compromise (BEC) and ransomware, which combined accounted for over 75% of cases responded to.
BEC investigations increased 86%, which was largely driven by adversaries continuing to bypass traditional security protections through the use of session token theft, QR code phishing and advanced persistence mechanisms within Microsoft365 (M365) tenancies.
Ransomware investigations doubled, with Threat Actors continuing to perform data exfiltration, data encryption and phone call/email harassment of victims.
Notably, from the Triskele Labs engagements, only 4.8% of victims paid a ransom, which is hopefully a sign of organisations improving their resilience to these kinds of attacks.
Healthcare and Finance Hit the Hardest
The healthcare and finance sectors were once again the most impacted, comprising nearly 30% of incidents responded to. The DFIR team observed factors such as legacy systems, remote access exposure and limited security investment continue to be the major cause of the breaches impacting these organisations.
Unsecured Remote Access Still a Key Entry Point
Ransomware initial access vectors remained consistent with previous years, with VPN and RDP without Multifactor Authentication (MFA) accounting for 60% of the initial access for ransomware groups.
Ransomware groups continue to utilise similar tactics – locating sensitive data stores within a network and performing data exfiltration utilising tools like Rclone, FileZilla and MEGASync, before encrypting systems.
The average amount of data exfiltrated from ransomware attacks was 381GB and frequently contained personally identifiable information (PII) and Protected Health Information (PHI) of both staff members and patients.
Threat Actors Are Getting Smarter
With BEC investigations, the DFIR team observed that Threat Actors would increasingly leverage mailbox synchronisation and delegate access, which can greatly increase the scope of an investigation and the impacted data sets.
There has also been a shift to advanced persistence measures such as the installation of custom Azure applications which highlights the need for targeted security controls prior to an incident and a proper forensic investigation when an incident does occur.
All Australian organisations, regardless of size or industry are potential targets for cyber security incidents. It is imperative for organisations to understand the risks that they face, continuously improve their security posture and adopt comprehensive security measures to protect their environments.
Background
This report presents statistics and information gathered from DFIR investigations conducted during the 2024-25 financial year. The data and insights are based on the work completed by the Triskele Labs DFIR Team, which has been operational for over four years.
Triskele Labs collaborates with numerous insurance carriers and law firms, providing specialised DFIR services that support legal and insurance claims related to cyber incidents. Our team works closely with these partners and clients to ensure thorough, accurate investigations that meet the necessary legal and regulatory standards.
The DFIR team has assisted hundreds of Australian organisations, ranging from small sole trader practices to large enterprise clients with thousands of servers and endpoints within their environments. This broad experience enables the team to effectively respond to all types of cyber incidents experienced by businesses.
Contributors
The Triskele Labs DFIR Team comprises experts located worldwide, enabling us to offer follow-the-sun forensic analysis capabilities. This round-the-clock coverage ensures organisations can quickly understand the nature and extent of cyber incidents, allowing them to take necessary steps to safely restore operations.
Our global presence facilitates continuous monitoring, rapid response, and effective threat mitigation, minimising downtime and enabling organisations to resume normal activities swiftly and securely.
We extend our gratitude to the Triskele Labs DFIR Team members for their invaluable contributions to this
Richard Grainger, Global Head of Digital Forensics
Craig Martin, Global Head of Incident Response
Chris McAdam, Incident Response Manager
Nick Thanos, Senior DFIR Analyst
Caleb Boyd, Senior DFIR Analyst
Jannis Herbst, DFIR Engineer
Michael Varley, DFIR Analyst
Jason Trapp, DFIR Analyst
Cameron Paddy, DFIR Analyst
Sarah Jordan, DFIR Analyst
Bailey Pearce, DFIR Analyst
Noraiz Mehboob, Associate DFIR Analyst
Jack Wigley, DFIR Analyst
Incident Statistics
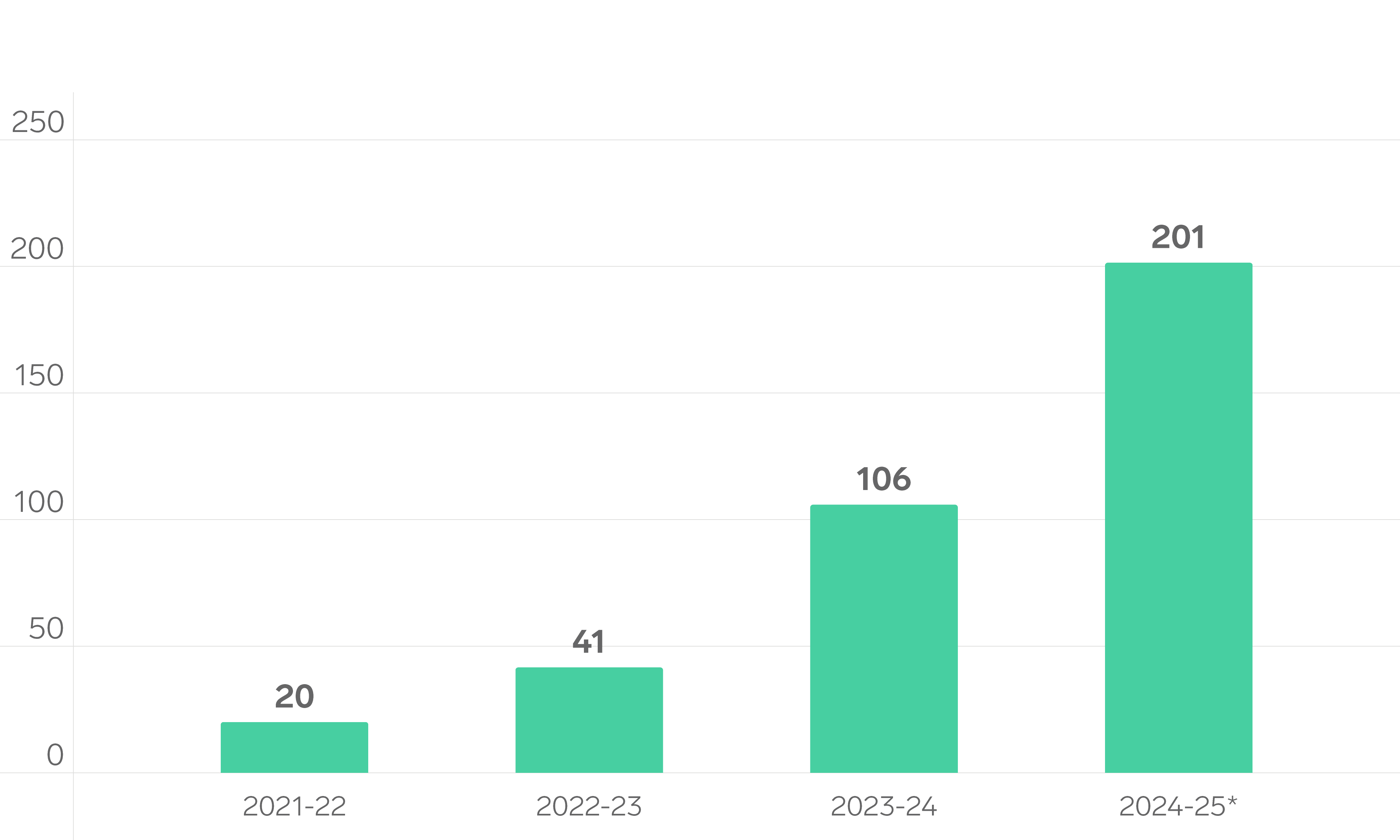
The Triskele Labs DFIR Team was engaged to perform 201 DFIR investigations over the 2024-25 financial year, representing an 89% increase from the 2023-24 financial year. This continuous rise in engagements underscores the prevalence of cyber incidents impacting Australian and New Zealand businesses.
Over the past four financial years, the team has handled a total of 368 investigations, demonstrating a consistent demand for DFIR services in addressing cyber security incidents.
Incident Heatmap
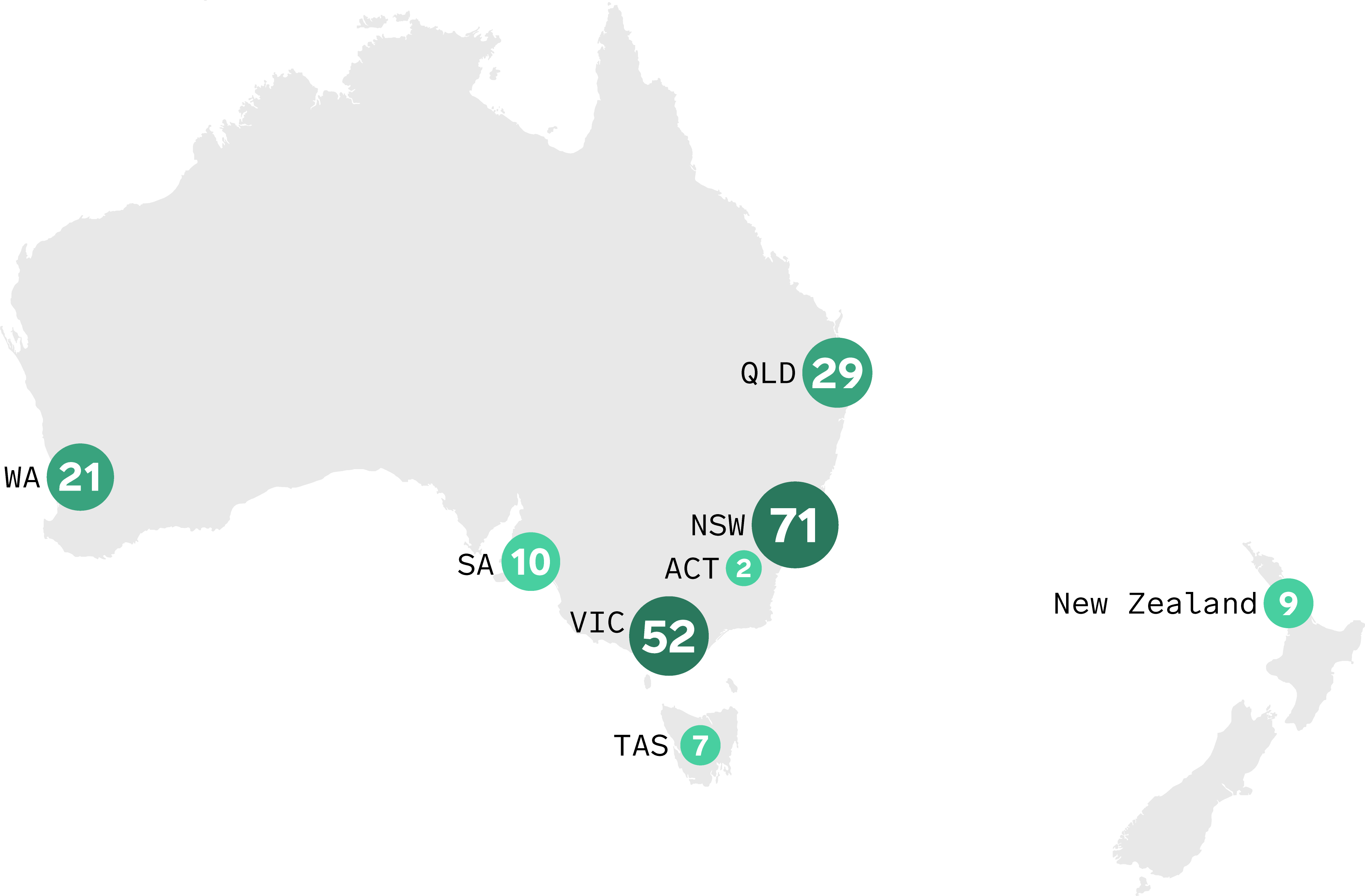
The Triskele Labs Digital Forensics and Incident Response (DFIR) Team responded to 201 cyber security incidents across capital cities in Australia and New Zealand over the past financial year.
New South Wales (NSW) had the highest number of incidents, overtaking last year’s leader Victoria (VIC) with 71 incidents. This represents a significant increase of 144% compared to the previous year. Victoria followed closely with 52 incidents, showing a 30% rise. Queensland (QLD) came in third with 29 incidents, demonstrating a year-on-year increase of 107%. This trend suggests that organisations with commercial head offices in Sydney may be based out of Queensland, given the state’s concentration of commercial entities.
These statistics underscore the persistent impact of cyber threats on businesses, regardless of their location. Whether operating in a major capital or a smaller city, organisations must prioritise robust cyber security measures to mitigate the risk of compromise.
Incident Types
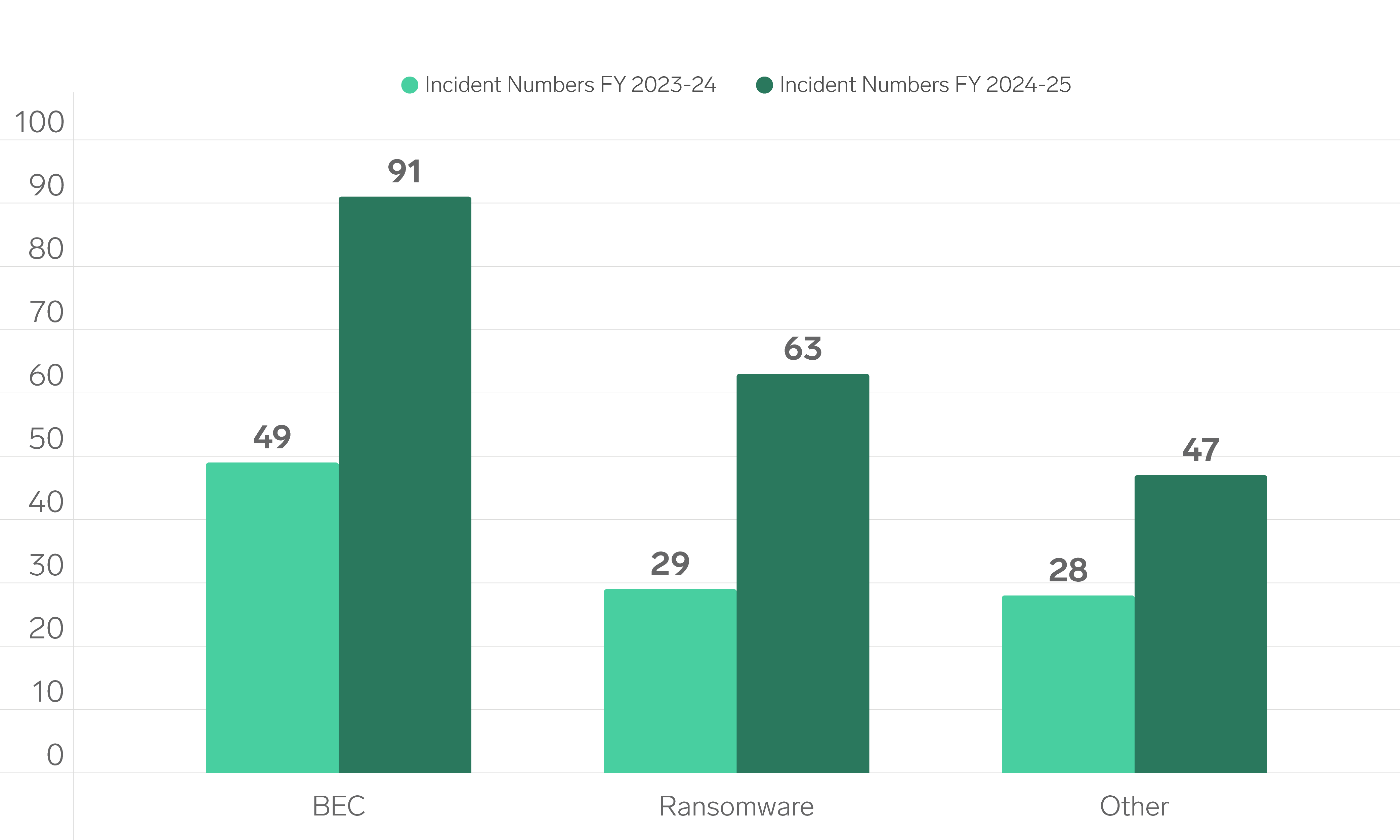
Over the past financial year, the Triskele Labs DFIR team has responded to a broad range of cyber incidents, from Business Email Compromise (BEC) and ransomware to insider threats and even unauthorised access to school systems aimed at modifying student grades.
Business Email Compromise
Business Email Compromise (BEC) was the most common incident type, with 91 cases recorded. This represents an 86% increase compared to the previous year. BEC attacks typically involve unauthorised access to business email accounts, often gained through phishing campaigns. Once access is obtained, attackers frequently attempt payment redirection fraud by impersonating legitimate stakeholders. These incidents can result in substantial financial losses and reputational harm. The high frequency of BEC cases underscores the importance of strong email security controls and ongoing user awareness training.
Ransomware
Ransomware also remained a significant threat, with 63 incidents recorded, marking a 117% rise from the previous financial year. These attacks commonly involve both the exfiltration of sensitive data and the encryption of critical systems. The operational and financial impacts can be severe, often leading to prolonged business disruption and potential data loss. Notably, 11 of these organisations detected the presence of the ransomware Threat Actor within their environment prior to any encryption taking place, allow for five of the victims to prevent the exfiltration of data.
Broader Incident Types
Beyond BEC and ransomware, the DFIR team also investigated 47 other cyber incidents. These included
- malware infections,
- insider threats,
- unauthorised access to data, and
- data breaches that did not fall specifically into the BEC or ransomware categories.
The data collected through these investigations provides critical insights into prevailing cyber threats and the effectiveness of existing controls.
By analysing the evidence collected, Triskele Labs can identify the real-world tactics, techniques and procedures (TTPs) used by threat actors.
This intelligence directly informs our containment and recovery strategies and enables us to deliver tailored, actionable advice to help clients improve their cyber resilience.
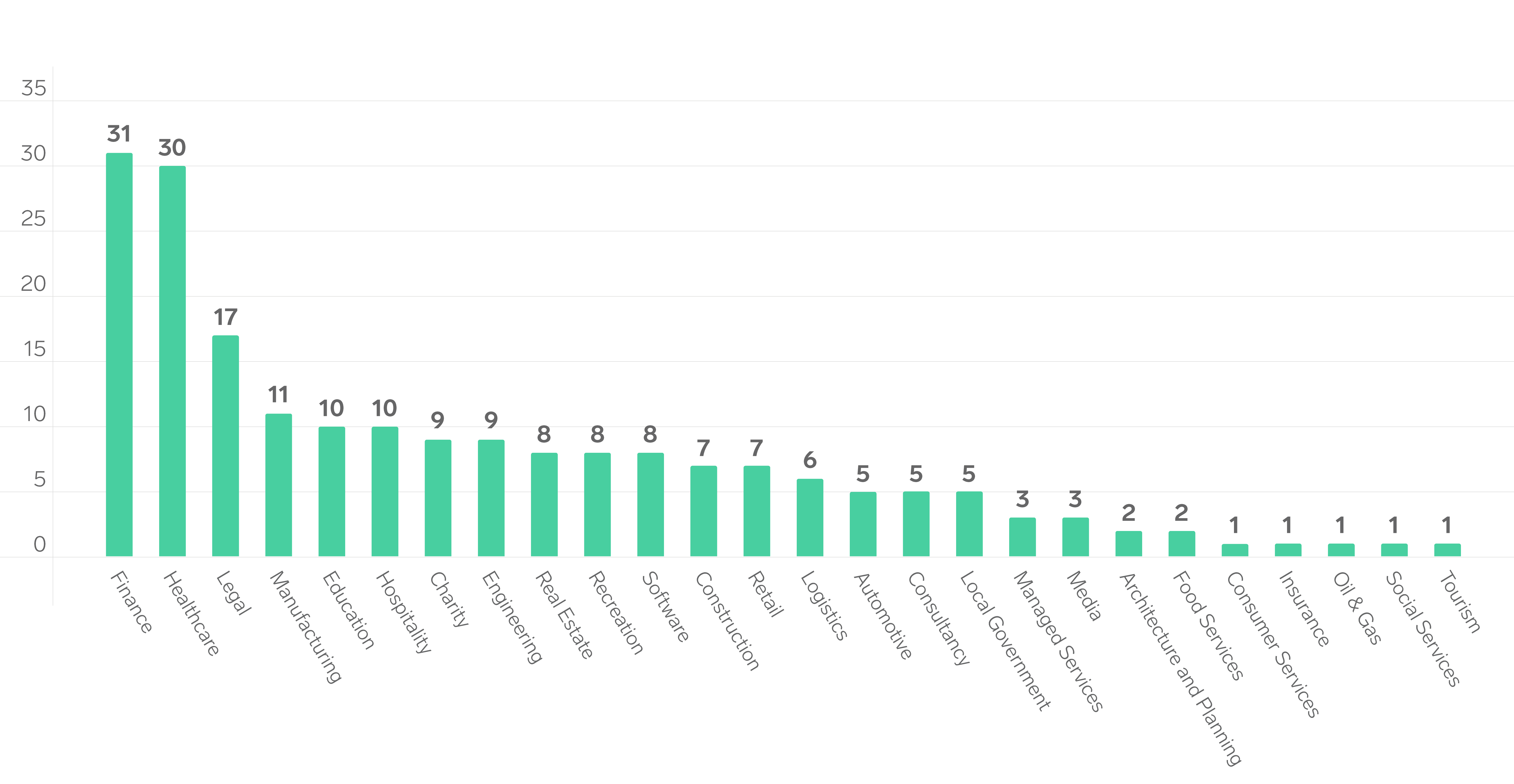
Industry Verticals
The Triskele Labs DFIR Team tracks incident data by industry vertical, revealing a key message: no sector is immune to cyber threats. Regardless of whether an organisation stores sensitive data or processes payments, it becomes a potential target for financially motivated Threat Actors.
Over the past financial year, the finance, healthcare, and legal sectors were the most affected.
- The finance sector recorded 31 incidents, representing a 47% increase from the previous year.
- Healthcare followed closely with 30 incidents, also showing a 130% rise.
- This year, the legal industry moved into third place, replacing real estate from last year, with 17 incidents. This reflects an increase of 183% compared to the previous financial year.
The high number of incidents in finance and healthcare may indicate weaker cyber security controls in these sectors, increasing their vulnerability to attack. Within the healthcare sector in particular, Triskele Labs has observed the continued use of end-of-life systems that support critical medical equipment. Many organisations are reluctant to upgrade these systems due to concerns about downtime or operational disruption, leaving them exposed to known security flaws.
Triskele Labs recommends that organisations ensure their systems are supported and regularly patched, especially when critical vulnerabilities are identified. Where immediate upgrades are not possible, compensating controls should be implemented to reduce the attack surface and manage the associated risk until the systems can be securely updated or replaced.
66% of malicious activity came from 'trusted' countries
Contrary to popular assumptions, most malicious activity did not originate from traditionally expected locations such as Russia, China, or parts of West Africa. Instead, Threat Actors frequently leveraged infrastructure based in more trusted regions to evade suspicion and avoid geo-blocking.
- 66% of IP addresses we attributed to Threat Actor activity in FY25 were located within Five Eyes (FVEY) countries: Australia, New Zealand, the United States, Canada, and the United Kingdom.
- Only 2% of attributed IPs were located in Russia.
- In total, we identified Threat Actor activity originating from 94 different countries.
This trend underscores that IP attribution alone is not a reliable indicator of Threat Actor origin. Attackers often employ compromised infrastructure, cloud services, and VPN exit nodes in trusted jurisdictions to conceal their true location.
Location alone is not a reliable indicator of malicious activity.
Many organisations still rely on basic geolocation-based alerting to flag suspicious access attempts. However, with a significant portion of Threat Actor IPs associated with Five Eyes countries, this approach is no longer sufficient. Threat Actors are increasingly using compromised infrastructure, cloud platforms, and residential proxies in trusted regions to bypass country-based detection rules.
If your security monitoring primarily flags “high-risk” regions like Russia or China, you are likely missing attacks occurring within your own borders.
Organisations must move beyond simple location filtering and focus on behavioural detection, access context, and anomaly correlation to effectively identify and respond to potential threats.
Case Study: Healthcare Provider
Initial Compromise via Insecure Remote Access
During the financial year, Triskele Labs responded to a ransomware incident that significantly impacted the operations of a healthcare provider. Initial access was gained using compromised credentials obtained by a Threat Actor conducting a brute-force password spraying attack against a Remote Desktop Gateway (RDG).
The RDG had been provisioned to allow medical practitioners, including doctors and external specialists, to remotely view patient test results. At the time of the incident, practitioners were only required to provide a valid username and password to gain access. MFA had not been configured for remote access.
Threat Actors commonly target RDGs that are not protected by MFA. Triskele Labs attributed 16 ransomware incidents this year to brute-force password spraying attacks on RDGs. RDGs do not natively support MFA, meaning additional configuration and planning is required outside of the scope of standard IT managed service arrangements.
Privilege Escalation and Unimpeded Data Exfiltration
Once inside the network, the Threat Actor conducted discovery activity to identify high-value systems. They successfully obtained credentials for a Domain Administrator account, enabling lateral movement and privilege escalation across the environment.
The practice had deployed a standard antivirus application as their sole cybersecurity control, which is a common choice among smaller medical practices due to cost constraints. While antivirus provides a basic line of defence against malware, it typically does not detect malicious actions such as credential harvesting, lateral movement, or data exfiltration. One of the most common actions during a ransomware deployment is the disabling or bypassing of antivirus. As antivirus products often lack tamper protection, the Threat Actor was able to disable the practice’s only security control without resistance.
With no other security tooling deployed, the Threat Actor was able to exfiltrate data from the environment without restriction. The practice relied on a shared file server to store patient information prior to uploading it into the Patient Management Software. Once uploaded, files were typically archived on the server. The Threat Actor accessed and exfiltrated a significant volume of sensitive patient records collected over the previous 15 years.
Throughout the two-week dwell time, the Threat Actor leveraged a range of malicious utilities and scripts. With antivirus disabled, no alerts were generated, and no-one at the practice was aware of the ongoing compromise.
Sector Specific Challenges
Once the Threat Actor had completed their objectives, they deployed ransomware and encrypted multiple servers across the environment, rendering them inaccessible. This was the first action that triggered visible disruption and ultimately led to the discovery of the compromise.
Medical practices commonly adopt limited cyber security protections, as their deployment increases complexity of the IT environment and subsequently ongoing maintenance costs.
- Medical examination rooms and Reception PCs will often use shared usernames and passwords to allow for quick access to information.
- Ad hoc storage locations are common, outside of defined Patient Management Software.
- When budgeting is considered, IT spend is commonly weighed against spending that will benefit patient health outcomes, leading to more limited cyber controls.
Ransomware Investigations
Overview
There is still a perception amongst organisations within Australia that ransomware is some sort of virus or malware that was inadvertently executed on systems by an unknowing staff member. Ransomware is a streamlined business that seeks to find the most efficient want to impacts as many organisations as possible.
The encryption observed as part of ransomware attacks is typically the last step undertaken as part of a Threat Actor’s attack and indicates that the Threat Actor has been successful in achieving their objectives.
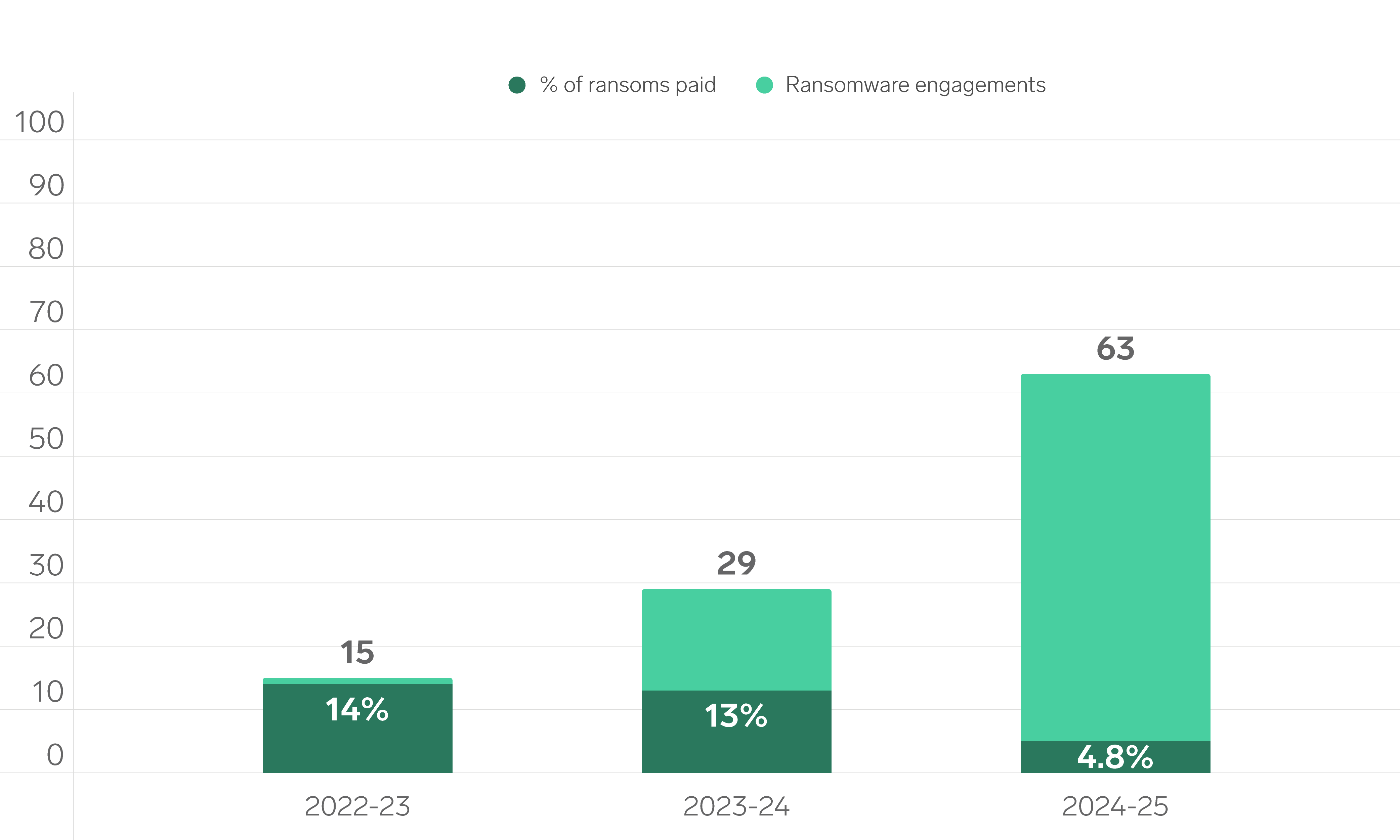
In total, Triskele Labs responded to 63 cyber incidents conducted by ransomware Threat Actors, which included:
- 52 successfully completed ransomware attacks.
- 11 interrupted ransomware attacks.
Double and Triple Extortion Tactics
Triskele Labs saw Threat Actors continuing to exfiltrate data in almost all available instances.
Threat Actors have also sought to continue to harass and interact with victims, via a number of common methods:
- Direct phone calls were placed with staff of the victim organisation, either via phone call to leadership teams or to publicly listed phone numbers (I.E. reception phone numbers).
- Emails are frequently being distributed to staff in order to raise the profile of the cyber attack across with wider employee population. In some instances, Threat Actors have been observed leveraging compromised internal email accounts in order to bypass email filters.
While Threat Actors routinely publish stolen data to dark web leak sites as part of double or triple extortion campaigns, a notable case this year demonstrated a more calculated approach.
In this instance, the Threat Actor took time to assess the victim’s backup configuration and identified specific data sets that were not being adequately backed up.
Rather than posting this data publicly, the Threat Actor explicitly informed the victim that these critical records would never be leaked a deliberate move to apply pressure by highlighting the organisations lack of recovery options. This tactic reflects an evolution in extortion strategy, shifting from broad public exposure to targeted psychological leverage, where the absence of backups becomes a vulnerability to be exploited, not just a technical gap.
The rise in email correspondence has led to a new breed of cyber criminals, who seek to email victims published on dark web leak sites and impersonate themselves as the Threat Actor. One group (loosely referred to as Foxxy Toxxy) will seek to impersonate high-profile ransomware Threat Actor groups and seek to initiate negotiations via a TOX chat. Just as organisations need to validate changing bank account details, it is now important to validate who a victim may be negotiating with.
Stages of a Typical Ransomware Attack
A typical ransomware attack generally follows several key stages:
- Initial Access: The Threat Actor will generally exploit a vulnerability or misconfiguration to gain entry into the network. Common methods include brute force attacks on exposed SSL VPN and RDP with no MFA, exploiting unpatched software vulnerabilities and phishing attacks.
- Privilege Escalation: Once inside the network, the attacker seeks to gain higher-level access. This is often achieved by exploiting additional vulnerabilities or using weak passwords to obtain domain administrator privileges.
- Discovery: The attacker scans the network to identify critical systems, backup locations, and sensitive data. This reconnaissance helps in planning the most impactful attack strategy.
- Persistence: To ensure continued access, the attacker installs backdoors or other persistence mechanisms. This allows them to re-enter the environment if initial access points are discovered and closed.
- Exfiltration: Sensitive data is exfiltrated to a server or file-sharing platform controlled by the attacker. This step is crucial in double and triple extortion tactics, where the threat of data exposure is used as leverage.
- Impact: The attacker deletes or disables backups and deploys ransomware to encrypt data across the network. This final step often includes a ransom note demanding payment in cryptocurrency for the decryption key. Threat Actors have also been incorporating triple extortion tactics, contacting employees, customers, regulators and even loss of infrastructure availability by conducting denial-of-service attacks (DoS) against publicly facing infrastructure.
Much of this activity goes undetected within victim environments. The average dwell time observed across all Triskele Labs’ ransomware engagements during the 2024/2025 financial year was 31 days, which was a decrease from 33 days last year.
Ransomware Groups
Within Australia, there were a few prolific ransomware groups that made headlines across the year:
Sarcoma, Qilin and Akira were all active across 2025 as they each posted seven Australian organisation on their leak sites. Based on engagements responded to by Triskele Labs, these Threat Actors sought to exploit vulnerable VPN and RDGs that were not protected by MFA.
Lynx had periods of high activity and named 8 Australian victims on their leak site across the FY. Information available publicly indicated that Lynx leveraged less-common techniques in order to bypass EDR in order to compromise larger victims with stronger controls.
Killsec3 was active across 2025, who were notable for leveraging some different tactics in order to achieve their objectives and exfiltrate and post data from seven victim environments.
Killsec3 were observed scanning for misconfigurations in cloud storage platforms in order to collect data that had inadvertently been made publicly accessible through misconfigurations.
The rise in Ransomware-as-a-Service (RaaS) has resulted in many affiliates moving between ransomware Threat Actor groups more actively. As a result, Triskele Labs have observed consistently applied TTPs across different Threat Actor groups, indicating that affiliates may be sharing knowledge and tooling with affiliates from different groups.
The same affiliate conducting across multiple different ransomware groups. Triskele Labs found one particular affiliate had conducted attacks under three 3 different ransomware groups in a nine month period.
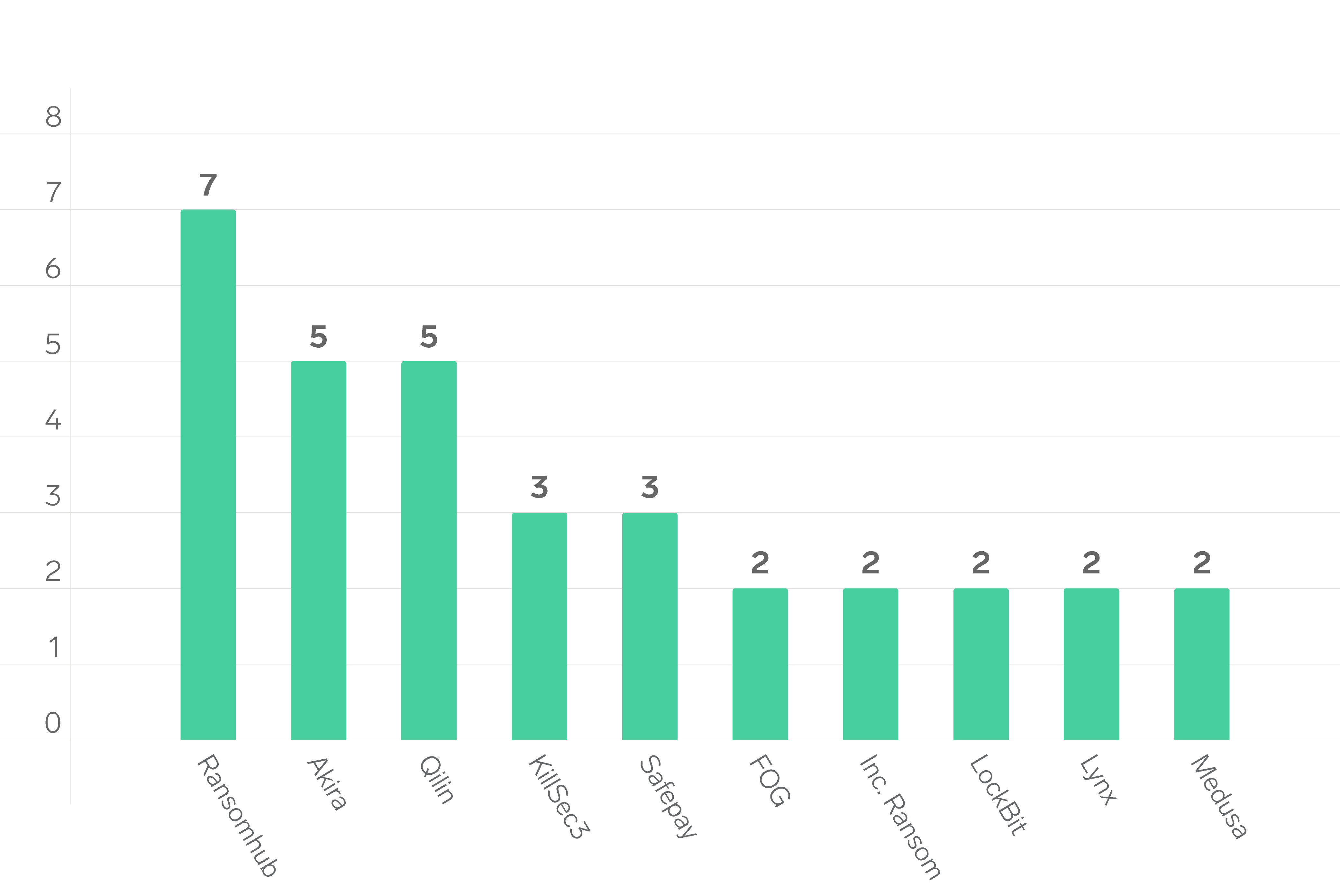
Across FY25, Triskele Labs are aware of at least 21 ransomware Threat Actor groups conducting multiple ransomware attacks against Australia / New Zealand businesses. Of these 21 groups, Triskele has responded to at least one ransomware matter for 17 of them in FY25.
For ten of these groups, Triskele Labs responded to more than one ransomware response, which featured:
- Ransomhub
- Akira
- Qilin
- KillSec3
- Safepay
- FOG
- Inc. Ransom
- LockBit
- Lynx
- Medusa
Group Spotlight: RansomHub
RansomHub emerged as the most active ransomware group targeting Australian organisations in FY25, with 13 victims listed on its leak site over the period. Triskele Labs directly responded to seven (7) RansomHub-related incidents, offering a unique insight into the group’s operational methods and tactics.
RansomHub's campaigns were marked by a clear shift toward more strategic and deliberate intrusions compared to other ransomware-as-a-service (RaaS) operations.
One of the most notable characteristics observed across RansomHub incidents was an unusually long dwell time. The group maintained persistence within victim environments for an average of 69 days prior to detection or encryption.
This extended presence allowed affiliates to undertake detailed reconnaissance and develop a nuanced understanding of the victim’s infrastructure. In particular, RansomHub operators were meticulous in their analysis of backup configurations, often identifying critical data that was not being captured and using this intelligence to exert maximum leverage during extortion attempts.
The group also demonstrated a high level of technical sophistication in maintaining access to compromised networks. Affiliates regularly deployed tunnelling tools such as Cloudflared, allowing them to bypass perimeter defences and establish resilient command-and-control channels.
Data exfiltration was almost exclusively conducted via Rclone, a tool commonly used for cloud storage synchronisation but repurposed by Threat Actors for large-scale data theft. This combination of stealth, persistence and operational maturity made RansomHub a particularly challenging adversary for incident responders.
In a surprising turn of events, RansomHub ceased operations in late March 2025, abruptly pulling its infrastructure from the dark web without warning.
Shortly after, the rival group DragonForce claimed that RansomHub had joined its platform, hinting at the formation of a decentralised “ransomware cartel” model. This move appeared to fragment the RansomHub affiliate network, with some affiliates migrating to other groups like Qilin, while others were left in limbo due to the lack of communication from the core operators. The sudden shutdown left many questions unanswered and raised broader concerns about the future trajectory of RaaS ecosystems and threat actor alliances.
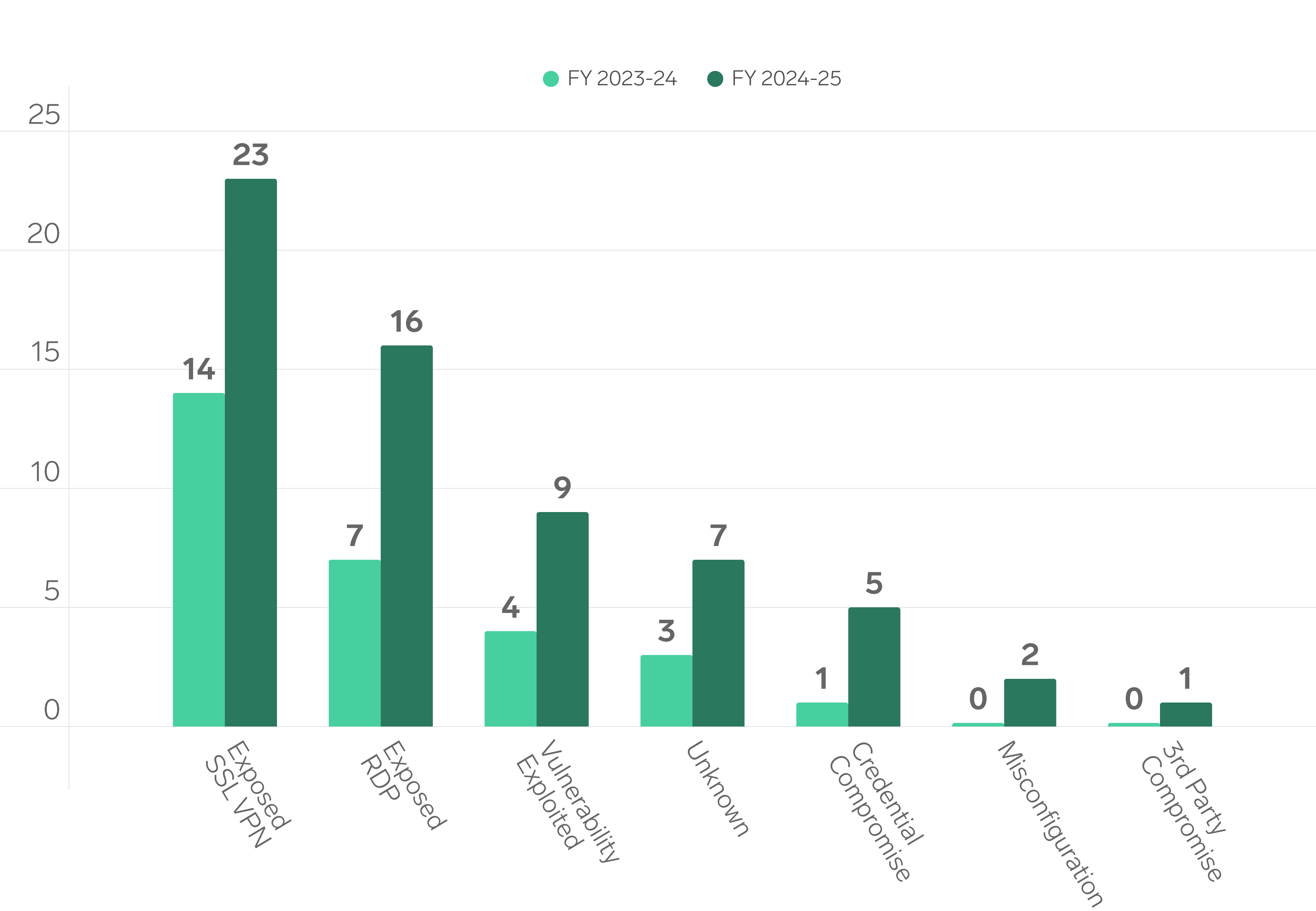
Initial Access
Exposed SSL VPN services without multi-factor authentication (MFA) remain the dominant initial access vector. In FY 2024-25 we recorded 23 incidents, up from 14 in the previous year, a 64 % increase. Organisations that leave these portals unprotected continue to offer attackers a simple way in.
RDP services exposed to the internet without MFA held second position. Incidents rose from seven to 16, which is a 129 % jump. Attackers still favour brute-force and credential-stuffing techniques against these gateways because they succeed far too often.
Exploitation of unpatched vulnerabilities climbed from four to nine incidents, a 125 % rise, moving this vector into third place. Patch management is still lagging: Microsoft Exchange servers vulnerable to ProxyShell, first disclosed in August 2021, are still being compromised in 2025.
Although misconfigurations and third-party compromises appear less frequently, they remain significant. Opportunistic groups such as KillSec3 scan for cloud misconfigurations like open S3 buckets and mass-exploit known flaws. Their CrushFTP campaign exfiltrated data worldwide without deploying ransomware, underscoring a shift toward pure data-theft operations.
We’ve also had increasing success in attributing initial access to information-stealing malware like LummaStealer. These attacks are especially effective in environments where organisations permit Bring Your Own Device (BYOD) practices or allow contractors to connect using non-corporate devices. In such cases, credentials harvested from unmanaged endpoints are later reused against corporate services.
These trends show attackers consistently pursue the path of least resistance. Enforcing MFA across all external-facing services, patching internet-facing assets promptly and applying strict device-access controls are essential steps to reduce exposure.
Data Exfiltration
Over the past financial year, we conducted a total of 63 ransomware investigations, with 52 of those cases involving confirmed data exfiltration. The confirmation of exfiltration activity was determined through a combination of network-based forensics, host-based forensics, and ISP metadata, which continue to be critical sources in identifying threat actor behaviour post-compromise. This highlights the ongoing trend where data theft is now a standard component of ransomware operations, not just encryption alone.
Limited Forensic Evidence in Some Cases
Despite strong visibility in many cases, 17 of the 63 engagements did not contain sufficient forensic artefacts to definitively identify the tooling used for exfiltration. This typically occurs when attackers clear logs, perform full disk encryption, or when endpoint or network visibility logging has short retention periods. This underscores the importance of comprehensive logging, monitoring, and endpoint detection to aid incident response investigations.
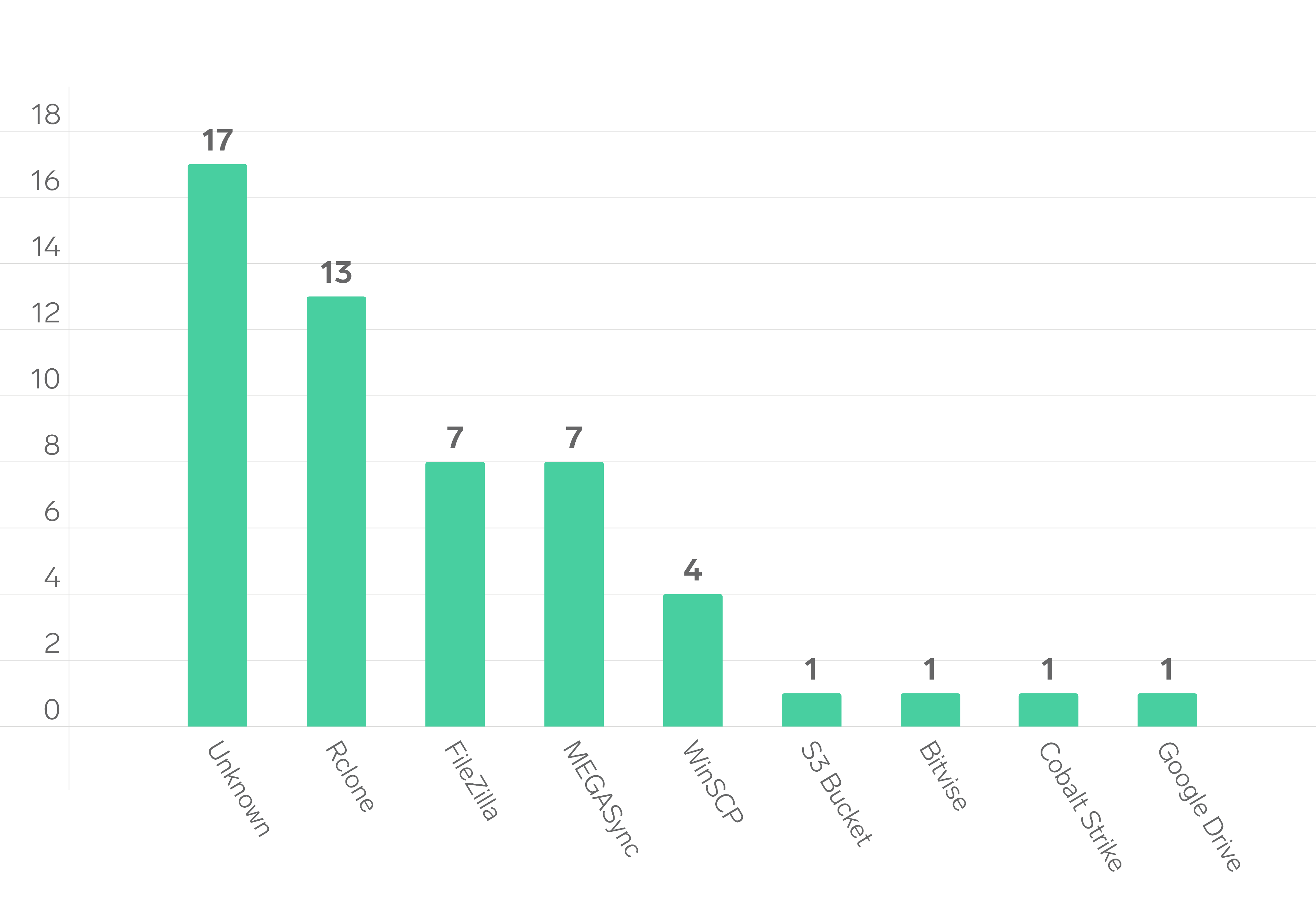
Preferred Tools: Rclone, Mega, and FileZilla
Among the cases where tooling could be confirmed, Rclone emerged as the most frequently used exfiltration tool, appearing in 13 engagements. Its versatility, command-line interface, and support for a wide range of cloud storage services make it a preferred choice for attackers. Following Rclone, Mega and FileZilla were tied in second place, each used in 7 engagements. These findings reflect a continued reliance on common, off-the-shelf tools by threat actors, likely to evade detection and blend into legitimate activity.
Volume of Data Exfiltrated
The average volume of data exfiltrated per confirmed engagement was 381 GB, representing a decrease from 406 GB observed in the previous financial year. While this drop is notable, it still demonstrates the significant impact of these incidents, particularly where sensitive or regulated data is involved.
Proactive Disruption of Threat Infrastructure
In several engagements, Triskele Labs successfully obtained credentials or configuration files linked to Threat Actor infrastructure, allowing for further action beyond immediate containment. These artefacts were promptly provided to Legal Incident Responders, enabling formal takedown requests to be issued, or were shared directly with Australian and international law enforcement agencies. In multiple instances, this led to the disruption of exfiltration infrastructure, including the successful removal of data repositories where stolen information was being held.
However, even where takedowns have been effective, data is still published in the vast majority of cases where a ransom payment is not negotiated. This reinforces the reality that Threat Actors maintain multiple copies of exfiltrated data, often across different platforms or locations. This was clearly illustrated in recent law enforcement operations targeting LockBit, where data persisted despite claims by the ransomware group that it had been deleted.
Assume Compromise — Always
These findings underscore the importance of assuming data is compromised once exfiltrated, regardless of whether it appears to have been removed, and reinforce the value of timely legal engagement during the incident response process.
Ransom Payments
The Decline of Payouts in 2025
The 2024–25 financial year saw a significant decline in ransom payments, continuing a positive trend in organisational resilience. Out of 63 ransomware investigations conducted, a ransom was paid in only three cases, representing just 4.8% of engagements. This is a marked drop from the 13% payment rate observed in the 2023–24 financial year, indicating both a shift in incident response decisions and growing confidence in recovery strategies.
Several contributing factors have been identified. Firstly, many victim organisations had robust backup and recovery capabilities in place, which enabled them to restore operations without needing to negotiate with Threat Actors. Secondly, a number of organisations were targeted by sanctioned ransomware groups, which made payment legally impossible, regardless of their ability to recover. In other cases, organisations assessed the cost of data recovery, including rebuilding from non-encrypted systems, offsite data, or prior exports and found it to be more economical than paying for a decryption tool. Finally, a growing number of organisations are taking a principled stance, refusing to pay on moral grounds in an effort to disrupt the ransomware business model and avoid reinforcing its profitability.
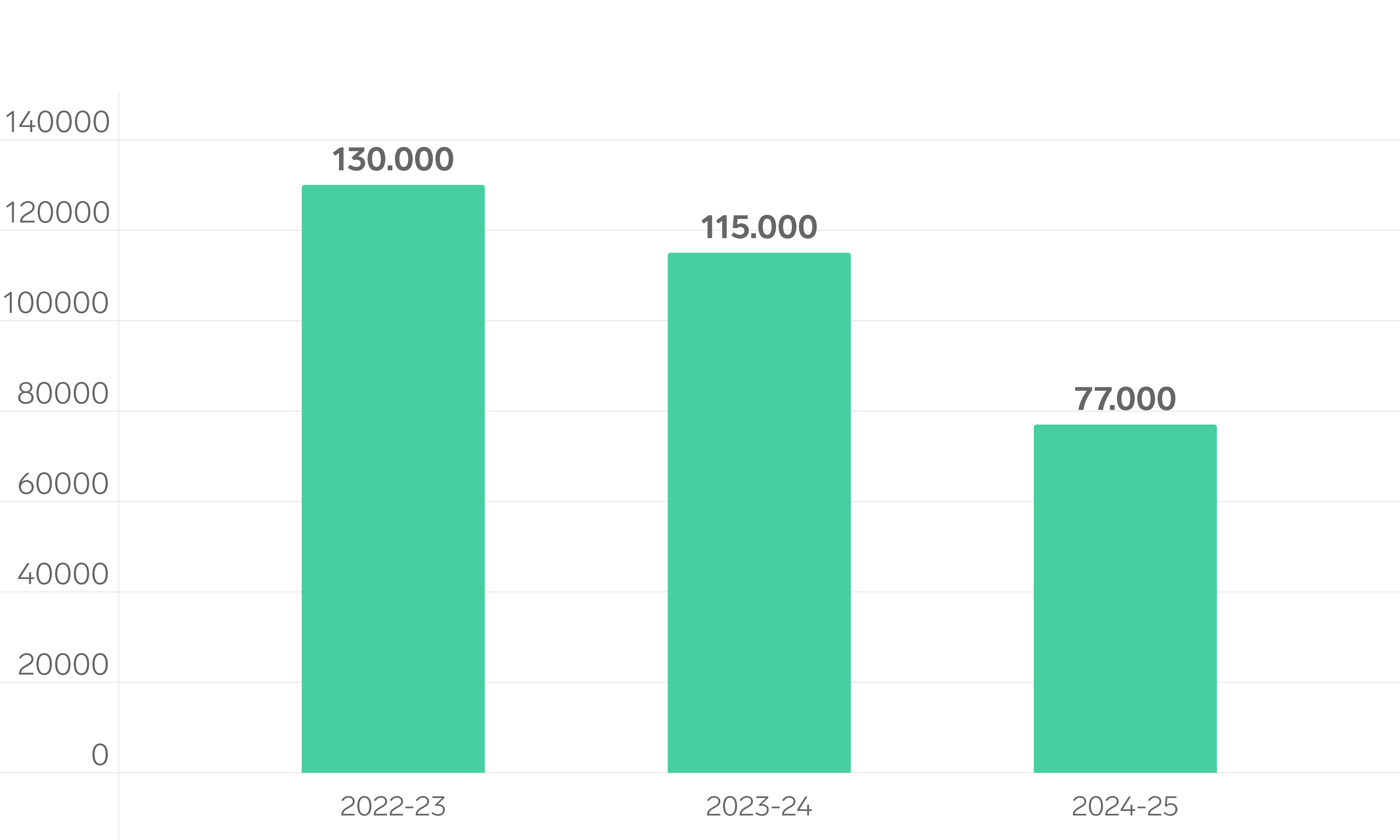
In addition to the reduced frequency of payments, the average ransom paid also declined. This year, the average payment was approximately $77,000 USD, down from $115,000 USD the previous year.
Ransomware Themes
Third Party Compromise
A recurring theme in this year’s ransomware investigations was the compromise of environments through third-party access. These compromises often stemmed from a lack of visibility and control over how service providers and contractors were interacting with internal systems. In many cases, Threat Actors were able to gain initial access by exploiting weaknesses in third-party systems.
We observed several systemic issues across environments impacted by third-party compromise:
- Many accounts were assigned to third party IT providers, which had been assigned full administrator privileges.
- Access into the client environment was permitted via unmanaged devices, in essence allowing for connections to originate from any location as long as the credentials were valid.
- No MFA enforcement had been applied for external access. One instance found an IT MSP had enforced MFA for all client connections, however excluded their own account from this requirement.
- Limited visibility of how and when the third-party was expected to connect into the client network.
In many instances, external parties were being treated as trusted insiders, but without the same controls or oversight applied to internal staff.
In one case, an organisation had experienced a ransomware incident as a result of a third-party credential compromises. Following the incident, the third-party was offboarded and the project was close. Despite this, appropriate steps were still not followed to disable the access assigned to the third-party. It was subsequently found that the organisation took weeks to disable access following the cessation of the contract.
A broader contributing factor was the absence of structured identity and access management. Many organisations lacked a centralised register of third-party accounts, did not log activity associated with external users accessing internal systems, and relied on informal processes to manage onboarding and offboarding.
Lack of monitoring
One of the most consistent findings in Triskele Labs' ransomware investigations this year was the absence of action associated with responding to security alerts. In nearly every case involving unauthorised access to infrastructure, there were early indicators or alerts raised as part of the compromise. These alerts either went unnoticed, were misinterpreted, or were simply never seen.
We observed environments where Endpoint Detection and Response (EDR) tooling was deployed and functioning, yet the alerts it generated were:
- Mis-triaged or ignored by Managed Security Service Providers (MSSPs), Managed Service Providers (MSPs), or internal IT teams. In one instance, an external provider of a ransomware victim directly warned the organisation that their environment had been compromised by a ransomware Threat Actor. This warning was ignored, and the organisation was subsequently encrypted less than 24 hours later.
- Being forwarded to inboxes or ticket queues that were not being actively monitored, or were being flooded with alerts from all security and IT platforms that resulted in significant alerts being downed out by noise.
- Generated outside of business hours, with no arrangements in place for after-hours monitoring or response.
In some incidents, the security tooling in place was not fit for purpose. Legacy antivirus or basic antimalware solutions were still being relied upon in enterprise environments, despite well-known limitations in detecting modern attacker behaviours such as credential theft, lateral movement, and scripting activity. These products were easily disabled or bypassed by Threat Actors during the early stages of compromise.
While technology was technically present in many cases, the real issue was operational. Many victims lacked defined processes, ownership, or appropriate resourcing that allowed small issues to become major breaches.
Password Hygiene
Credential misuse and poor access control remain some of the most consistent themes observed during ransomware investigations. In far too many cases, initial access or privilege escalation was gained not through sophisticated actions but through basic oversights that centred around weak passwords, shared accounts, and the absence of appropriate password controls.
It was common to encounter spreadsheets full of credentials stored in shared drives, often unprotected and accessible to anyone with network access. We regularly saw variants of the same passwords reused widely across environments, including between user and administrator accounts and across both production and backup environments. These practices made lateral movement trivial for Threat Actors once they gained an initial foothold.
Many organisations had no formal process to offboard staff or disable expired accounts, leaving unused credentials lingering for months or years. In environments without identity management, oversight of administrator accounts was often not performed at all.
The cumulative effect of these practices has led to Threat Actor leveraging basic techniques, including manually searching through shared drives, in order to elevate privileged. threat landscape where attackers don’t need to be particularly sophisticated. While Triskele Labs has observed many organisations increasing their spending on cyber security controls, there are still weakness centred around the behaviour of users within environments.
Business Email Compromise (BEC) Investigations
Overview
Business Email Compromise (BEC) incidents represented 45% of all incidents handled by Triskele Labs in the 2024-25 financial year. Although the operational impact of BEC incidents is generally less severe than that of ransomware attacks, the financial consequences can be substantial, especially when payment direction fraud is involved.
These attacks responded to by Triskele Labs predominantly target victims using the Microsoft 365 (M365) suite of business productivity applications (I.E. Microsoft Outlook), reflecting its dominance as the primary platform for business communications in Australia and New Zealand.
Understanding Business Email Compromise
The vast majority of BEC incidents observed across investigations are performed by Threat Actors that are financially motivated.
- The most common outcome is payment redirection fraud, where attackers impersonate suppliers, executives, or staff to trick victims into transferring funds to attacker-controlled accounts.
- In some cases, the compromise is leveraged to scam downstream individuals or partner organisations, further amplifying the impact.
The impactful nature of financially motivated Threat Actors remained the primary driver of detection for BECs, which was most commonly detected as a result of:
- The business detecting attempted or successful payment redirection fraud conducted by the Threat Actor.
- The business is alerted to suspicious emails being sent by the Threat Actor to external parties, typically in the form of phishing emails that have been distributed in an attempt by the Threat Actor to extend their access to new victims.
BECs associated with solely information gathering objectives were rarely observed, in part due to the less impactful nature of these Threat Actors and the fact that they are less common amongst Australian small and medium businesses. Financially motivated Threat Actors continue to use techniques that result in the access and collection of information from mailbox users and the risk of this taking place as part of BECs remains, even when it is not the primary motivation of the Threat Actor.
Threat Actors are leveraging techniques designed to establish and exploit trust. Phishing campaigns typically sent once the Threat Actor has exhausted opportunities to complete payment redirection fraud within a compromised impacts, are most commonly observed issuing out phishing emails to known contacts of the compromised mailbox.
Instead of sending a malicious attachment or direction users to a suspicious URL, it is becoming increasingly common for Threat Actor to create documents within the legitimate file sharing platforms of the compromised account (I.E. SharePoint, OneDrive, Dropbox) and sharing access to the document. Receiving a link to a document hosted within a legitimate sharing location, from a known contact, is resulting in Threat Actors furthering their access to new victims.
Role of Forensics
Digital Forensics and Incident Response (DFIR) investigations are conducted with extensive experience and knowledge of the investigative process. DFIR acts as an external, trusted party focused on delivering unbiased, fact-based insights critical to understanding cyber incidents. While internal IT staff or external IT Managed Service Providers provide valuable support, often investigations do not capture the nuanced details and techniques that an investigation requires.
The objectives of a DFIR BEC investigation typically are to:
- Confirm that there had been unauthorised access to mailbox(es).
- Identify how the Threat Actor was able to gain initial access to the environment.
- Identify what actions were performed by the Threat Actor whilst they had access.
- Identify whether Personally Identifiable Information (PII) or Protected Health Information (PHI) had been accessed by the Threat Actor.
- Ensure that the Threat Actor has been purged from the environment.
- Provide guidance with the remediation and recovery activities.
- Provide recommendations to strengthen the cyber security posture post incident.
Traditional investigation methods are increasingly falling short, particularly given the growing complexity of Business Email Compromise BEC techniques. Notably, Threat Actors are now employing persistence mechanisms not observed in previous financial years, allowing them to maintain access even after standard containment and investigative measures have been applied.
Stages of a Business Email Compromise
Initial Access
Over the past financial year, Threat Actors have increasingly leveraged legitimate infrastructure, such as free hosting platforms, to host redirection and landing pages. These pages are often customised to match the branding of the compromised organisation, including their logo and business name. Because they are hosted on legitimate services and typically contain only a secondary link (rather than a direct credential harvester), they frequently bypass email filtering controls.
The delivery of phishing campaigns is widely being facilitated through legitimate services such as SharePoint, DropBox and MailChimp. Files that contain a link to a credential harvester will be uploaded to the legitimate platform, where the Threat Actor will subsequently leverage the platform’s share functionality to distribute access to the file to victims. Some platforms also include the ability to schedule follow-up reminders, which can further continue the phishing emails delivery.
Threat Actors have been observed applying MFA to external SaaS solutions (I.E. DropBox, MailChimp) in order to prevent the legitimate account holders from regain access to the account.
QR code phishing (or 'quishing') remains in use, although it is currently less prevalent than the newer delivery methods described above.
Evidence Sources
As of 1 March 2025, Microsoft stopped writing audit log data directly to mailboxes. From this date forward, activity attributed to actions performed within an account is only captured within Unified Audit Log (UAL), under the condition that UAL is enabled. For Microsoft 365 tenancies created after 2021, the UAL is enabled by default. However, tenants created in 2021 or earlier will not have this enabled by default.
To check whether UAL is enabled, a privileged account holder can visit https://purview.microsoft.com and navigate to the ‘Audit’ section. If the UAL is not enabled, a blue banner will appear prompting you to turn it on. Enabling it may take several minutes to take effect.
Alternatively, UAL status can be verified using PowerShell:
- Run Connect-ExchangeOnline to authenticate.
- Enter Get-AdminAuditLogConfig to retrieve the audit log configuration.
- Review the fields UnifiedAuditLogIngestionEnabled and UnifiedAuditLogFirstOptInDate to determine if the UAL is active and when it was enabled.
- If not enabled, you can enable it by running: Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
Data Exfiltration
A critical part of a Business Email Compromise (BEC) investigation is determining whether mailbox synchronisation has occurred, as this process creates a local offline copy of the mailbox. While synchronisation is designed to improve productivity by allowing users to access emails even without internet connectivity. This functionality has also introduced risk during mailbox compromises as Threat Actors can obtain a complete copy of any mailbox contents.
Delegate access is another key consideration. Within many organisations, it is common for users to be granted access to shared mailboxes or other employees’ mailboxes for operational purposes. If a compromised user account has such access, the impact of the incident can quickly expand beyond a single mailbox, increasing the overall risk and complexity of the investigation.
Email clients like Microsoft Outlook automatically create an Offline Outlook Data File (OST) when a user signs in, storing emails, calendar events and contacts on the local device. This means that a Threat Actor who signs into a compromised mailbox using the Outlook desktop application can generate a full local copy of the mailbox—accessible even after containment measures are applied.
Third-party applications like eM Client provide similar functionality and are sometimes used by Threat Actors to send and receive emails from compromised accounts. eM Client supports full mailbox synchronisation, with the default configuration set to synchronise all messages excluding attachments. However, it can be adjusted to download full mailbox contents, including attachments, to the local device.
Threat Actors may also leverage legitimate cloud backup tools such as PerfectData Software to exfiltrate mailbox data. PerfectData enables complete mailbox backups from various services, including Microsoft 365 and IMAP. When used maliciously, this allows a Threat Actor to extract an entire mailbox during the window of compromise, often before any containment or recovery actions have been taken.
Persistence
One of the more advanced techniques observed in Business Email Compromise (BEC) cases for the first time this financial year was the use of Azure App Registrations to maintain persistence within Microsoft 365 environments. This technique allows Threat Actors to create an authorised application that can access mailbox data and other M365 resources via Graph API, even after credentials are reset or MFA is enforced. It is particularly effective in scenarios where traditional containment measures (I.E. password resets) are applied without a thorough investigation. In these cases, the Threat Actor can silently retain access to the environment.
In 28% of BEC cases investigated across the financial year, Triskele Labs identified some form of persistence mechanism being leveraged. Azure App Registrations were a notable trend, closely mirroring the capabilities of offensive tooling like GraphRunner, which is designed to abuse Graph API permissions. Other persistence techniques included the use of Temporary Access Passes (TAPs), the creation of new Microsoft 365 accounts, and the reactivation or password reset of dormant or inactive accounts.
These findings reinforce the need for a deeper investigative approach when responding to BEC incidents. If containment is completed without identifying and removing the mechanisms Threat Actors have established for persistence, organisations risk ongoing unauthorised access and further compromise.
Payment Redirection Fraud
Once a mailbox has been compromised, the primary motivation of the Threat Actor is typically to conduct payment redirection fraud. In many cases, the compromised organisation itself facilitates the attempt by providing the attacker with access to email conversations, invoice templates, and contact details for clients. Threat Actors use this access to impersonate the organisation in an attempt to deceive clients into transferring funds to attacker-controlled bank accounts.
However, it's increasingly common for the compromised organisation to become the victim of the fraud itself. Threat Actors are frequently registering lookalike domains to impersonate trusted suppliers or service providers, allowing them to target accounts payable teams within a legitimate business. Many organisations are drawn in through convincing emails that appear to originate from a legitimate source, with only subtle indicators of fraud. This reinforces the importance of human controls that include validating bank detail changes through a known phone number, using multi-party approval workflows for financial transactions, and training staff to identify red flags. While technical controls can reduce risk, it is often these manual validation steps that prevent fraudulent payments from being made.
Payment redirection fraud was attempted in 27% of Business Email Compromise (BEC) cases investigated by Triskele Labs over the financial year. Of those cases, Threat Actors successfully achieved their objective in 40% of attempts, highlighting the effectiveness of this tactic when detection and human validation controls fail.
On average, successful attempts resulted in the redirection of $107,927 which represented the significant financial impact that can arise from a single compromised mailbox or supplier impersonation.
Detection
Most BEC incidents are first identified in one of two ways:
- Receipt of an external notification following phishing emails sent from the compromised account; or
- An internal discovery due to delayed payments or financial discrepancies.
The delayed and reactive nature of these detection methods means Threat Actors are often able to operate within the environment unnoticed for an extended period. Across cases investigated by Triskele Labs, the average dwell time before detection was 32 days (down from 41 days in the previous financial year), with most incidents only identified once the attacker took an action that caused visible impact.
Payment Redirection Fraud
Once a mailbox has been compromised, the primary motivation of the Threat Actor is typically to conduct payment redirection fraud. In many cases, the compromised organisation itself facilitates the attempt by providing the attacker with access to email conversations, invoice templates, and contact details for clients. Threat Actors use this access to impersonate the organisation in an attempt to deceive clients into transferring funds to attacker-controlled bank accounts.
However, it's increasingly common for the compromised organisation to become the victim of the fraud itself. Threat Actors are frequently registering lookalike domains to impersonate trusted suppliers or service providers, allowing them to target accounts payable teams within a legitimate business. Many organisations are drawn in through convincing emails that appear to originate from a legitimate source, with only subtle indicators of fraud. This reinforces the importance of human controls that include validating bank detail changes through a known phone number, using multi-party approval workflows for financial transactions, and training staff to identify red flags. While technical controls can reduce risk, it is often these manual validation steps that prevent fraudulent payments from being made.
Payment redirection fraud was attempted in 27% of Business Email Compromise (BEC) cases investigated by Triskele Labs over the financial year. Of those cases, Threat Actors successfully achieved their objective in 40% of attempts, highlighting the effectiveness of this tactic when detection and human validation controls fail. On average, successful attempts resulted in the redirection of $107,927 which represented the significant financial impact that can arise from a single compromised mailbox or supplier impersonation.
Detection
MostBEC incidents are first identified in one of two ways:
- Receipt of an external notification following phishing emails sent from the compromised account; or
- An internal discovery due to delayed payments or financial discrepancies.
The delayed and reactive nature of these detection methods means Threat Actors are often able to operate within the environment unnoticed for an extended period.Across cases investigated by Triskele Labs, the average dwell time before detection was 32 days (down from 41 days in the previous financial year), with most incidents only identified once the attacker took an action that caused visible impact.
PaymentRedirection Fraud
Once a mailbox has been compromised, the primary motivation of the Threat Actor is typically to conduct payment redirection fraud. In many cases, the compromised organisation itself facilitates the attempt by providing the attacker with access to email conversations, invoice templates, and contact details for clients. Threat Actors use this access to impersonate the organisation in an attempt to deceive clients into transferring funds to attacker-controlled bank accounts.
However, it's increasingly common for the compromised organisation to become the victim of the fraud itself. Threat Actors are frequently registering lookalike domains to impersonate trusted suppliers or service providers, allowing them to target accounts payable teams within a legitimate business. Many organisations are drawn in through convincing emails that appear to originate from a legitimate source, with only subtle indicators of fraud. This reinforces the importance of human controls that include validating bank detail changes through a known phone number, using multi-party approval workflows for financial transactions, and training staff to identify red flags.While technical controls can reduce risk, it is often these manual validation steps that prevent fraudulent payments from being made.
Payment redirection fraud was attempted in 27% of Business Email Compromise (BEC) cases investigated by Triskele Labs over the financial year. Of those cases, ThreatActors successfully achieved their objective in 40% of attempts, highlighting the effectiveness of this tactic when detection and human validation controls fail.
On average, successful attempts resulted in the redirection of $107,927 which represented the significant financial impact that can arise from a single compromised mailbox or supplier impersonation.
BEC Themes
Session Token Theft
While the uptake of Multifactor Authentication (MFA) continues slowly across Australia, Across Australia and New Zealand, many businesses are implementing MFA as there it has been a common belief that MFA will mitigate the risk of credential compromise. Unfortunately, Threat Actors are continuing to embed techniques within their technology to bypass these MFA controls, particularly within the Microsoft 365 platform due to it’s prevalence of use across the industry.
Session token theft is a form of Adversary-in-the-Middle (AitM) attack whereby a Threat Actor will develop a credential harvester that impersonates the Microsoft 365 authentication portal. As a victim enters their legitimate username, password and MFA token within the credential harvester, the information is used to legitimate authenticate into Microsoft 365 in order to collect an authorised session token.
Many users are on the lookout for suspicious emails or poorly coded authentication portals, however the technologies in use by Threat Actors are bypassing these perceptions of the public and resulting in successful email compromises.
In one instance across FY25, the leader of a small business has been championing cyber awareness within their organisation and led a 12 month education and training program amongst staff. At the end of this program, the leader fell victim to a phishing campaign that leveraged common techniques. Information provided by the leader found that these common techniques had not been included as part of the provided training.
The techniques used by Threat Actors are streamlined and being used frequently to conduct attacks which can be shared with staff easily to increase awareness and build the cyber resilience of organisations.
Mobile Devices
While the convenience offered by accessing emails from your phone is seen as a positive for many business leaders, it also introduces an additional risk when it comes of the proliferation of BECs and payment redirection fraud.
- Many common email applications designed for mobile devices will only show the senders email name, not the full email address. This has been a contributing factor in many BECs across FY25, where the recipient of the email does not identify that a Threat Actor is impersonating the email address of an external contact.
- It is common for staff to use personal mobile devices which are not managed by the organisation. Actions associated with interactions with phishing emails or malicious attachments are not detected by the organisation’s security tooling.
- Some Threat Actor continue to leverage QR codes as a mechanism to deliver credential harvesters, which are designed to initiate activity from mobile devices, instead of managed laptops and endpoints.
Excessive Permissions
Particularly common across small businesses, Triskele Labs has found that many businesses and user accounts are being assigned excessive (or top level) administrative privileges within email environments.
Larger organisations have mature processes in place that necessitate the implementation of Identity and Access Management, Principles of Least Privilege and dedicated Service Accounts for administrative users. For smaller businesses, it is not uncommon for leaders or office administrators to be assigned administrative permissions that are commonly being exploited by Threat Actors.
In one instance recently responded to by Triskele Labs, an IT user was assigned temporary top level privileges within their Microsoft 365 tenancy in order to complete an upgrade project. During these period of elevated access, the user’s account was compromised by a Threat Actor. Leveraging the top-level privileges, the Threat Actor commandeered the entire Microsoft 365 and Azure Cloud tenancy of the business and locked legitimate business users out of the environment entirely.
Many users assigned top-level privileges (I.E. Microsoft 365’s Global Administrator role) do not require the full use to the assigned permissions and would benefit from being assigned a role with fewer account privileges.
Even for standard user accounts, there are privileges commonly assigned that are being exploited by Threat Actors to enable the rapid access and collection of information from the mailbox user. Microsoft 365 allows for users to authenticate to third-party applications in order to interact with their accounts in different ways; Threat Actors are frequently exploiting this permission and authenticating to applications designed to collect copies of mailboxes, extract information from mailboxes or issue mass phishing campaigns from mailboxes.
Key BEC Controls
There are some common controls Triskele Labs recommends to mitigate the likelihood and impact of BECs affecting organisations:
- Enforce Multi-Factor Authentication to protect again unsophisticated attack methods (I.E. credential stuffing).
- Implement policies to restrict access to resources from outside of expected locations or services (I.E. Geoblocking policies, third-party applications, unauthorised devices)
- Segregate administrative access to platforms to dedicated non-user accounts.
- Assess the opportunities to implement session token protection controls.
- Implement 24x7 monitoring in order to detect unusual sign-in activities.
- Govern how third-party administrative access is being assigned and monitored.
Emerging Risks
Lack of Encryption
The emergence of ransomware Threat Actors that don’t encrypt data. Throughout FY25, Triskele Labs identified two (2) Threat Actors that obtained sufficient access to internal systems to allow for encryption to be deployed, however the Threat Actor was observed actively choosing not to encrypt victim environments:
- One Threat Actor made assertions of their leak site that while they did compromise and extort victims across all industry verticals, they did not encrypt the environments of healthcare providing organisations. Triskele Labs noted that this Threat Actor followed this rule on one (1) occasions, whilst breaking in earlier in the year for other healthcare providing victims.
- A new Threat Group emerged in FY25 that does not seek to encrypt victims. Instead of encrypting systems and making them unavailable, this Threat Actor solely exfiltrates data and relies on organisations seeking to pay in order to prevent the data from being published.
Further to this, examples were identified of Threat Actors, notably KillSec3, conducting exfiltration attacks against publicly accessible data stores and vulnerable File Transfer Protocol (FPT) servers. During these attacks, the Threat Actor sought to exfiltrate unprotected data from these locations and publish the data on their Dark Web leak site. In manage instances the organisation was unaware that the incident had occurred until the name of the organisation was listed on a Dark Web leak site.
With many organisations not applying appropriate controls to personal, sensitive or health information, Threat Actors are presented with less barriers to exfiltrate data than they are to encrypt systems.
Key Controls:
- Network restrictions to prevent open internet access from infrastructure.
- Adoption of Data Loss Prevention (DLP) controls.
- Strong Identify and Access Management (IAM) controls restricting unnecessary access. permissions within the environment.
- Data encryption at risk.
- Secure configuration and management of file storage and file transfer infrastructure.
Endpoint Compromise
Throughout FY25, Triskele Labs responded to multiple cyber incidents that originated from endpoint compromises.
In one example, Triskele Labs successfully attributed a ransomware attack to the deployment of credential stealing software that was deployed to an unmanaged device.
Across FY24 and FY25, Triskele Labs observed ransomware Threat Actors exploiting weaknesses within external access controls (I.E. lack of MFA configured for remote access) in order to establish access within victim environments. Once environments were compromised, Threat Actors would remain connected to server infrastructure in order to complete their attacks.
In order to allow staff to fulfill the requirements of their role, it is not uncommon for Endpoints to be provisioned with less restrictive access controls. Threat Actors were observed leveraged user endpoints across FY25 to exfiltrate data and bypass administrative access controls.
Key Controls:
- Restrict unmanaged devices from directly connecting to enterprise resources (I.E. BYOD).
- Deploy Enterprise Password Vaults to encourage good password hygiene and prevent passwords from being stored within insecure repositories like web browsers.
- Provision alternative access methods into environments for third parties (I.E. Managed RMM, Citrix Workspaces)
- Strength segregation between server infrastructure and user endpoints.
Unreported Incidents
Within FY25, three ransomware incidents were investigated by Triskele Labs where external IT Managed Service Providers did not inform their customers of significant cyber incidents.
- Three MSPs did not tell customers that their environment had been victim to a ransomware incident, instead advising customers that their environment had experienced an IT disruption.
Key contributing factors observed across these cases included:
- Security alerts were generated but not reviewed or escalated, despite opportunities to detect and contain the threat early.
- Basic preventative or detective controls (e.g. MFA, endpoint detection, segmentation) were missing or inconsistently implemented across the environments.
- Agreements between the client and provider often lacked clarity around roles and responsibilities during a security incident. In some cases, newly formed relationships or commercial pressures appeared to influence disclosure decisions.
These incidents highlight a persistent and growing risk where third-party IT providers fail to meet their obligations during cyber events. The absence of clear contractual responsibilities and inconsistently applied security controls increases the likelihood of cyber incidents occurring and continues to leave companies exposed.
Importantly, this trend aligns with a broader shift in appetite from both insurers and victim organisations to pursue financial recovery or compensation from third parties whose failures contributed to an incident. With changes to the Australian Privacy Act expanding enforcement powers and introducing higher penalties for serious or repeated interferences with privacy, it is likely that FY26 will see increased legal and financial scrutiny of external service providers involved in cyber events.
Organisations are more frequently assessing the contractual, operational, and legal accountability of IT vendors post-incident, particularly where early intervention could have mitigated or prevented harm.
Key Controls:
- Ensure service agreements clearly require third parties to report security incidents within defined timeframes and cooperate during investigations.
- Implement shared visibility into critical security alerts so clients retain awareness of detections within the environment.
- Seek the support of an external party in order to establish whether the controls implemented by an MSP are appropriate.
Conclusion
The 2024–25 financial year highlighted a clear shift in the scale and consistency of cyber incidents impacting organisations across Australia and New Zealand. From endless BEC campaigns where phishing emails are being distributed to further the access of a Threat Actor, to highly disruptive ransomware attacks, Threat Actors demonstrated their ability to evade detection and exploit weaknesses within organisations in order to achieve their objectives. These incidents reinforce the need for proactive, not reactive, security strategies.
Culture, Awareness and Leadership Accountability
The most resilient organisations in FY26 will be those that treat cybersecurity as a shared responsibility. Security is not just an IT issue. Staff at all levels need to understand their role in preventing and responding to threats. Awareness programs need to go beyond basic phishing simulations and focus on real-world techniques used by attackers, including credential theft and social engineering.
Leadership also plays a critical role. Boards and senior executives must ensure that cybersecurity is prioritised, appropriately resourced, and governed. A lack of engagement at the top has been a common factor in many of the most damaging incidents Triskele Labs responded to. Cyber risk is now a core business risk.
Governance, Resilience and Recovery Planning
Many of the incidents Triskele Labs investigated during the year were preventable. Controls were often partially implemented, misconfigured, or poorly monitored. In some cases, legacy systems or third-party access created hidden risk due to weak governance and oversight.
Resilience is not just about stopping attacks. It also means being able to detect and respond to threats at any time. Backups should be tested regularly. Business continuity plans need to be updated to reflect current threats and realistic recovery timelines. Proactive security operations and well-defined response processes are essential.
Implementation, Integration and Monitoring
Core technical controls like MFA, endpoint protection and data loss prevention remain critical. However, having tools in place is not enough. They must be properly configured, monitored, and integrated with operational processes. Misconfigurations and gaps in visibility were key factors in many incidents.
In 2024–25, Threat Actors consistently exploited these weaknesses to gain access, move through networks undetected, and deploy ransomware or exfiltrate sensitive data. A layered and well-integrated technology stack is vital for early detection and effective response.
Executive Summary
The 2024-25 financial year saw a large rise in the number and scale of cyber incidents affecting Australian and New Zealand organisations. The Triskele Labs Digital Forensics and Incident Response (DFIR) team responded to 201 incidents that impacted small, medium and enterprise organisations across the region.
This year’s report, once again, provides real statistics from incidents responded to, helping organisations understand how to protect themselves.
BEC and Ransomware Dominate the Threat Landscape
Across industries and geographies, the majority of incidents stemmed from Business Email Compromise (BEC) and ransomware, which combined accounted for over 75% of cases responded to.
BEC investigations increased 86%, which was largely driven by adversaries continuing to bypass traditional security protections through the use of session token theft, QR code phishing and advanced persistence mechanisms within Microsoft365 (M365) tenancies.
Ransomware investigations doubled, with Threat Actors continuing to perform data exfiltration, data encryption and phone call/email harassment of victims.
Notably, from the Triskele Labs engagements, only 4.8% of victims paid a ransom, which is hopefully a sign of organisations improving their resilience to these kinds of attacks.
Healthcare and Finance Hit the Hardest
The healthcare and finance sectors were once again the most impacted, comprising nearly 30% of incidents responded to. The DFIR team observed factors such as legacy systems, remote access exposure and limited security investment continue to be the major cause of the breaches impacting these organisations.
Unsecured Remote Access Still a Key Entry Point
Ransomware initial access vectors remained consistent with previous years, with VPN and RDP without Multifactor Authentication (MFA) accounting for 60% of the initial access for ransomware groups.
Ransomware groups continue to utilise similar tactics – locating sensitive data stores within a network and performing data exfiltration utilising tools like Rclone, FileZilla and MEGASync, before encrypting systems.
The average amount of data exfiltrated from ransomware attacks was 381GB and frequently contained personally identifiable information (PII) and Protected Health Information (PHI) of both staff members and patients.
Threat Actors Are Getting Smarter
With BEC investigations, the DFIR team observed that Threat Actors would increasingly leverage mailbox synchronisation and delegate access, which can greatly increase the scope of an investigation and the impacted data sets.
There has also been a shift to advanced persistence measures such as the installation of custom Azure applications which highlights the need for targeted security controls prior to an incident and a proper forensic investigation when an incident does occur.
All Australian organisations, regardless of size or industry are potential targets for cyber security incidents. It is imperative for organisations to understand the risks that they face, continuously improve their security posture and adopt comprehensive security measures to protect their environments.
Background
This report presents statistics and information gathered from DFIR investigations conducted during the 2024-25 financial year. The data and insights are based on the work completed by the Triskele Labs DFIR Team, which has been operational for over four years.
Triskele Labs collaborates with numerous insurance carriers and law firms, providing specialised DFIR services that support legal and insurance claims related to cyber incidents. Our team works closely with these partners and clients to ensure thorough, accurate investigations that meet the necessary legal and regulatory standards.
The DFIR team has assisted hundreds of Australian organisations, ranging from small sole trader practices to large enterprise clients with thousands of servers and endpoints within their environments. This broad experience enables the team to effectively respond to all types of cyber incidents experienced by businesses.
Contributors
The Triskele Labs DFIR Team comprises experts located worldwide, enabling us to offer follow-the-sun forensic analysis capabilities. This round-the-clock coverage ensures organisations can quickly understand the nature and extent of cyber incidents, allowing them to take necessary steps to safely restore operations.
Our global presence facilitates continuous monitoring, rapid response, and effective threat mitigation, minimising downtime and enabling organisations to resume normal activities swiftly and securely.
We extend our gratitude to the Triskele Labs DFIR Team members for their invaluable contributions to this
Richard Grainger, Global Head of Digital Forensics
Craig Martin, Global Head of Incident Response
Chris McAdam, Incident Response Manager
Nick Thanos, Senior DFIR Analyst
Caleb Boyd, Senior DFIR Analyst
Jannis Herbst, DFIR Engineer
Michael Varley, DFIR Analyst
Jason Trapp, DFIR Analyst
Cameron Paddy, DFIR Analyst
Sarah Jordan, DFIR Analyst
Bailey Pearce, DFIR Analyst
Noraiz Mehboob, Associate DFIR Analyst
Jack Wigley, DFIR Analyst
Incident Statistics
The Triskele Labs DFIR Team was engaged to perform 201 DFIR investigations over the 2024-25 financial year, representing an 89% increase from the 2023-24 financial year. This continuous rise in engagements underscores the prevalence of cyber incidents impacting Australian and New Zealand businesses.
Over the past four financial years, the team has handled a total of 368 investigations, demonstrating a consistent demand for DFIR services in addressing cyber security incidents.

Incident Heatmap
The Triskele Labs Digital Forensics and Incident Response (DFIR) Team responded to 201 cyber security incidents across capital cities in Australia and New Zealand over the past financial year.
New South Wales (NSW) had the highest number of incidents, overtaking last year’s leader Victoria (VIC) with 71 incidents. This represents a significant increase of 144% compared to the previous year. Victoria followed closely with 52 incidents, showing a 30% rise. Queensland (QLD) came in third with 29 incidents, demonstrating a year-on-year increase of 107%. This trend suggests that organisations with commercial head offices in Sydney may be based out of Queensland, given the state’s concentration of commercial entities.
These statistics underscore the persistent impact of cyber threats on businesses, regardless of their location. Whether operating in a major capital or a smaller city, organisations must prioritise robust cyber security measures to mitigate the risk of compromise.

Incident Types
Over the past financial year, the Triskele Labs DFIR team has responded to a broad range of cyber incidents, from Business Email Compromise (BEC) and ransomware to insider threats and even unauthorised access to school systems aimed at modifying student grades.
Business Email Compromise
Business Email Compromise (BEC) was the most common incident type, with 91 cases recorded. This represents an 86% increase compared to the previous year. BEC attacks typically involve unauthorised access to business email accounts, often gained through phishing campaigns. Once access is obtained, attackers frequently attempt payment redirection fraud by impersonating legitimate stakeholders. These incidents can result in substantial financial losses and reputational harm. The high frequency of BEC cases underscores the importance of strong email security controls and ongoing user awareness training.
Ransomware
Ransomware also remained a significant threat, with 63 incidents recorded, marking a 117% rise from the previous financial year. These attacks commonly involve both the exfiltration of sensitive data and the encryption of critical systems. The operational and financial impacts can be severe, often leading to prolonged business disruption and potential data loss. Notably, 11 of these organisations detected the presence of the ransomware Threat Actor within their environment prior to any encryption taking place, allow for five of the victims to prevent the exfiltration of data.
Broader Incident Types
Beyond BEC and ransomware, the DFIR team also investigated 47 other cyber incidents. These included
- malware infections,
- insider threats,
- unauthorised access to data, and
- data breaches that did not fall specifically into the BEC or ransomware categories.
The data collected through these investigations provides critical insights into prevailing cyber threats and the effectiveness of existing controls.
By analysing the evidence collected, Triskele Labs can identify the real-world tactics, techniques and procedures (TTPs) used by threat actors.
This intelligence directly informs our containment and recovery strategies and enables us to deliver tailored, actionable advice to help clients improve their cyber resilience.

Industry Verticals
The Triskele Labs DFIR Team tracks incident data by industry vertical, revealing a key message: no sector is immune to cyber threats. Regardless of whether an organisation stores sensitive data or processes payments, it becomes a potential target for financially motivated Threat Actors.
Over the past financial year, the finance, healthcare, and legal sectors were the most affected.
- The finance sector recorded 31 incidents, representing a 47% increase from the previous year.
- Healthcare followed closely with 30 incidents, also showing a 130% rise.
- This year, the legal industry moved into third place, replacing real estate from last year, with 17 incidents. This reflects an increase of 183% compared to the previous financial year.
The high number of incidents in finance and healthcare may indicate weaker cyber security controls in these sectors, increasing their vulnerability to attack. Within the healthcare sector in particular, Triskele Labs has observed the continued use of end-of-life systems that support critical medical equipment. Many organisations are reluctant to upgrade these systems due to concerns about downtime or operational disruption, leaving them exposed to known security flaws.
Triskele Labs recommends that organisations ensure their systems are supported and regularly patched, especially when critical vulnerabilities are identified. Where immediate upgrades are not possible, compensating controls should be implemented to reduce the attack surface and manage the associated risk until the systems can be securely updated or replaced.
66% of malicious activity came from 'trusted' countries
Contrary to popular assumptions, most malicious activity did not originate from traditionally expected locations such as Russia, China, or parts of West Africa. Instead, Threat Actors frequently leveraged infrastructure based in more trusted regions to evade suspicion and avoid geo-blocking.
- 66% of IP addresses we attributed to Threat Actor activity in FY25 were located within Five Eyes (FVEY) countries: Australia, New Zealand, the United States, Canada, and the United Kingdom.
- Only 2% of attributed IPs were located in Russia.
- In total, we identified Threat Actor activity originating from 94 different countries.
This trend underscores that IP attribution alone is not a reliable indicator of Threat Actor origin. Attackers often employ compromised infrastructure, cloud services, and VPN exit nodes in trusted jurisdictions to conceal their true location.
Location alone is not a reliable indicator of malicious activity.
Many organisations still rely on basic geolocation-based alerting to flag suspicious access attempts. However, with a significant portion of Threat Actor IPs associated with Five Eyes countries, this approach is no longer sufficient. Threat Actors are increasingly using compromised infrastructure, cloud platforms, and residential proxies in trusted regions to bypass country-based detection rules.
If your security monitoring primarily flags “high-risk” regions like Russia or China, you are likely missing attacks occurring within your own borders.
Organisations must move beyond simple location filtering and focus on behavioural detection, access context, and anomaly correlation to effectively identify and respond to potential threats.

Case Study: Healthcare Provider
Initial Compromise via Insecure Remote Access
During the financial year, Triskele Labs responded to a ransomware incident that significantly impacted the operations of a healthcare provider. Initial access was gained using compromised credentials obtained by a Threat Actor conducting a brute-force password spraying attack against a Remote Desktop Gateway (RDG).
The RDG had been provisioned to allow medical practitioners, including doctors and external specialists, to remotely view patient test results. At the time of the incident, practitioners were only required to provide a valid username and password to gain access. MFA had not been configured for remote access.
Threat Actors commonly target RDGs that are not protected by MFA. Triskele Labs attributed 16 ransomware incidents this year to brute-force password spraying attacks on RDGs. RDGs do not natively support MFA, meaning additional configuration and planning is required outside of the scope of standard IT managed service arrangements.
Privilege Escalation and Unimpeded Data Exfiltration
Once inside the network, the Threat Actor conducted discovery activity to identify high-value systems. They successfully obtained credentials for a Domain Administrator account, enabling lateral movement and privilege escalation across the environment.
The practice had deployed a standard antivirus application as their sole cybersecurity control, which is a common choice among smaller medical practices due to cost constraints. While antivirus provides a basic line of defence against malware, it typically does not detect malicious actions such as credential harvesting, lateral movement, or data exfiltration. One of the most common actions during a ransomware deployment is the disabling or bypassing of antivirus. As antivirus products often lack tamper protection, the Threat Actor was able to disable the practice’s only security control without resistance.
With no other security tooling deployed, the Threat Actor was able to exfiltrate data from the environment without restriction. The practice relied on a shared file server to store patient information prior to uploading it into the Patient Management Software. Once uploaded, files were typically archived on the server. The Threat Actor accessed and exfiltrated a significant volume of sensitive patient records collected over the previous 15 years.
Throughout the two-week dwell time, the Threat Actor leveraged a range of malicious utilities and scripts. With antivirus disabled, no alerts were generated, and no-one at the practice was aware of the ongoing compromise.
Sector Specific Challenges
Once the Threat Actor had completed their objectives, they deployed ransomware and encrypted multiple servers across the environment, rendering them inaccessible. This was the first action that triggered visible disruption and ultimately led to the discovery of the compromise.
Medical practices commonly adopt limited cyber security protections, as their deployment increases complexity of the IT environment and subsequently ongoing maintenance costs.
- Medical examination rooms and Reception PCs will often use shared usernames and passwords to allow for quick access to information.
- Ad hoc storage locations are common, outside of defined Patient Management Software.
- When budgeting is considered, IT spend is commonly weighed against spending that will benefit patient health outcomes, leading to more limited cyber controls.
Ransomware Investigations
Overview
There is still a perception amongst organisations within Australia that ransomware is some sort of virus or malware that was inadvertently executed on systems by an unknowing staff member. Ransomware is a streamlined business that seeks to find the most efficient want to impacts as many organisations as possible.
The encryption observed as part of ransomware attacks is typically the last step undertaken as part of a Threat Actor’s attack and indicates that the Threat Actor has been successful in achieving their objectives.
In total, Triskele Labs responded to 63 cyber incidents conducted by ransomware Threat Actors, which included:
- 52 successfully completed ransomware attacks.
- 11 interrupted ransomware attacks.
Double and Triple Extortion Tactics
Triskele Labs saw Threat Actors continuing to exfiltrate data in almost all available instances.
Threat Actors have also sought to continue to harass and interact with victims, via a number of common methods:
- Direct phone calls were placed with staff of the victim organisation, either via phone call to leadership teams or to publicly listed phone numbers (I.E. reception phone numbers).
- Emails are frequently being distributed to staff in order to raise the profile of the cyber attack across with wider employee population. In some instances, Threat Actors have been observed leveraging compromised internal email accounts in order to bypass email filters.
While Threat Actors routinely publish stolen data to dark web leak sites as part of double or triple extortion campaigns, a notable case this year demonstrated a more calculated approach.
In this instance, the Threat Actor took time to assess the victim’s backup configuration and identified specific data sets that were not being adequately backed up.
Rather than posting this data publicly, the Threat Actor explicitly informed the victim that these critical records would never be leaked a deliberate move to apply pressure by highlighting the organisations lack of recovery options. This tactic reflects an evolution in extortion strategy, shifting from broad public exposure to targeted psychological leverage, where the absence of backups becomes a vulnerability to be exploited, not just a technical gap.
The rise in email correspondence has led to a new breed of cyber criminals, who seek to email victims published on dark web leak sites and impersonate themselves as the Threat Actor. One group (loosely referred to as Foxxy Toxxy) will seek to impersonate high-profile ransomware Threat Actor groups and seek to initiate negotiations via a TOX chat. Just as organisations need to validate changing bank account details, it is now important to validate who a victim may be negotiating with.
Stages of a Typical Ransomware Attack
A typical ransomware attack generally follows several key stages:
- Initial Access: The Threat Actor will generally exploit a vulnerability or misconfiguration to gain entry into the network. Common methods include brute force attacks on exposed SSL VPN and RDP with no MFA, exploiting unpatched software vulnerabilities and phishing attacks.
- Privilege Escalation: Once inside the network, the attacker seeks to gain higher-level access. This is often achieved by exploiting additional vulnerabilities or using weak passwords to obtain domain administrator privileges.
- Discovery: The attacker scans the network to identify critical systems, backup locations, and sensitive data. This reconnaissance helps in planning the most impactful attack strategy.
- Persistence: To ensure continued access, the attacker installs backdoors or other persistence mechanisms. This allows them to re-enter the environment if initial access points are discovered and closed.
- Exfiltration: Sensitive data is exfiltrated to a server or file-sharing platform controlled by the attacker. This step is crucial in double and triple extortion tactics, where the threat of data exposure is used as leverage.
- Impact: The attacker deletes or disables backups and deploys ransomware to encrypt data across the network. This final step often includes a ransom note demanding payment in cryptocurrency for the decryption key. Threat Actors have also been incorporating triple extortion tactics, contacting employees, customers, regulators and even loss of infrastructure availability by conducting denial-of-service attacks (DoS) against publicly facing infrastructure.
Much of this activity goes undetected within victim environments. The average dwell time observed across all Triskele Labs’ ransomware engagements during the 2024/2025 financial year was 31 days, which was a decrease from 33 days last year.
Ransomware Groups
Within Australia, there were a few prolific ransomware groups that made headlines across the year:
Sarcoma, Qilin and Akira were all active across 2025 as they each posted seven Australian organisation on their leak sites. Based on engagements responded to by Triskele Labs, these Threat Actors sought to exploit vulnerable VPN and RDGs that were not protected by MFA.
Lynx had periods of high activity and named 8 Australian victims on their leak site across the FY. Information available publicly indicated that Lynx leveraged less-common techniques in order to bypass EDR in order to compromise larger victims with stronger controls.
Killsec3 was active across 2025, who were notable for leveraging some different tactics in order to achieve their objectives and exfiltrate and post data from seven victim environments.
Killsec3 were observed scanning for misconfigurations in cloud storage platforms in order to collect data that had inadvertently been made publicly accessible through misconfigurations.
The rise in Ransomware-as-a-Service (RaaS) has resulted in many affiliates moving between ransomware Threat Actor groups more actively. As a result, Triskele Labs have observed consistently applied TTPs across different Threat Actor groups, indicating that affiliates may be sharing knowledge and tooling with affiliates from different groups.
The same affiliate conducting across multiple different ransomware groups. Triskele Labs found one particular affiliate had conducted attacks under three 3 different ransomware groups in a nine month period.
Across FY25, Triskele Labs are aware of at least 21 ransomware Threat Actor groups conducting multiple ransomware attacks against Australia / New Zealand businesses. Of these 21 groups, Triskele has responded to at least one ransomware matter for 17 of them in FY25.
For ten of these groups, Triskele Labs responded to more than one ransomware response, which featured:
- Ransomhub
- Akira
- Qilin
- KillSec3
- Safepay
- FOG
- Inc. Ransom
- LockBit
- Lynx
- Medusa

Group Spotlight: RansomHub
RansomHub emerged as the most active ransomware group targeting Australian organisations in FY25, with 13 victims listed on its leak site over the period. Triskele Labs directly responded to seven (7) RansomHub-related incidents, offering a unique insight into the group’s operational methods and tactics.
RansomHub's campaigns were marked by a clear shift toward more strategic and deliberate intrusions compared to other ransomware-as-a-service (RaaS) operations.
One of the most notable characteristics observed across RansomHub incidents was an unusually long dwell time. The group maintained persistence within victim environments for an average of 69 days prior to detection or encryption.
This extended presence allowed affiliates to undertake detailed reconnaissance and develop a nuanced understanding of the victim’s infrastructure. In particular, RansomHub operators were meticulous in their analysis of backup configurations, often identifying critical data that was not being captured and using this intelligence to exert maximum leverage during extortion attempts.
The group also demonstrated a high level of technical sophistication in maintaining access to compromised networks. Affiliates regularly deployed tunnelling tools such as Cloudflared, allowing them to bypass perimeter defences and establish resilient command-and-control channels.
Data exfiltration was almost exclusively conducted via Rclone, a tool commonly used for cloud storage synchronisation but repurposed by Threat Actors for large-scale data theft. This combination of stealth, persistence and operational maturity made RansomHub a particularly challenging adversary for incident responders.
In a surprising turn of events, RansomHub ceased operations in late March 2025, abruptly pulling its infrastructure from the dark web without warning.
Shortly after, the rival group DragonForce claimed that RansomHub had joined its platform, hinting at the formation of a decentralised “ransomware cartel” model. This move appeared to fragment the RansomHub affiliate network, with some affiliates migrating to other groups like Qilin, while others were left in limbo due to the lack of communication from the core operators. The sudden shutdown left many questions unanswered and raised broader concerns about the future trajectory of RaaS ecosystems and threat actor alliances.
Initial Access
Exposed SSL VPN services without multi-factor authentication (MFA) remain the dominant initial access vector. In FY 2024-25 we recorded 23 incidents, up from 14 in the previous year, a 64 % increase. Organisations that leave these portals unprotected continue to offer attackers a simple way in.
RDP services exposed to the internet without MFA held second position. Incidents rose from seven to 16, which is a 129 % jump. Attackers still favour brute-force and credential-stuffing techniques against these gateways because they succeed far too often.
Exploitation of unpatched vulnerabilities climbed from four to nine incidents, a 125 % rise, moving this vector into third place. Patch management is still lagging: Microsoft Exchange servers vulnerable to ProxyShell, first disclosed in August 2021, are still being compromised in 2025.
Although misconfigurations and third-party compromises appear less frequently, they remain significant. Opportunistic groups such as KillSec3 scan for cloud misconfigurations like open S3 buckets and mass-exploit known flaws. Their CrushFTP campaign exfiltrated data worldwide without deploying ransomware, underscoring a shift toward pure data-theft operations.
We’ve also had increasing success in attributing initial access to information-stealing malware like LummaStealer. These attacks are especially effective in environments where organisations permit Bring Your Own Device (BYOD) practices or allow contractors to connect using non-corporate devices. In such cases, credentials harvested from unmanaged endpoints are later reused against corporate services.
These trends show attackers consistently pursue the path of least resistance. Enforcing MFA across all external-facing services, patching internet-facing assets promptly and applying strict device-access controls are essential steps to reduce exposure.

Data Exfiltration
Over the past financial year, we conducted a total of 63 ransomware investigations, with 52 of those cases involving confirmed data exfiltration. The confirmation of exfiltration activity was determined through a combination of network-based forensics, host-based forensics, and ISP metadata, which continue to be critical sources in identifying threat actor behaviour post-compromise. This highlights the ongoing trend where data theft is now a standard component of ransomware operations, not just encryption alone.
Limited Forensic Evidence in Some Cases
Despite strong visibility in many cases, 17 of the 63 engagements did not contain sufficient forensic artefacts to definitively identify the tooling used for exfiltration. This typically occurs when attackers clear logs, perform full disk encryption, or when endpoint or network visibility logging has short retention periods. This underscores the importance of comprehensive logging, monitoring, and endpoint detection to aid incident response investigations.
Preferred Tools: Rclone, Mega, and FileZilla
Among the cases where tooling could be confirmed, Rclone emerged as the most frequently used exfiltration tool, appearing in 13 engagements. Its versatility, command-line interface, and support for a wide range of cloud storage services make it a preferred choice for attackers. Following Rclone, Mega and FileZilla were tied in second place, each used in 7 engagements. These findings reflect a continued reliance on common, off-the-shelf tools by threat actors, likely to evade detection and blend into legitimate activity.
Volume of Data Exfiltrated
The average volume of data exfiltrated per confirmed engagement was 381 GB, representing a decrease from 406 GB observed in the previous financial year. While this drop is notable, it still demonstrates the significant impact of these incidents, particularly where sensitive or regulated data is involved.
Proactive Disruption of Threat Infrastructure
In several engagements, Triskele Labs successfully obtained credentials or configuration files linked to Threat Actor infrastructure, allowing for further action beyond immediate containment. These artefacts were promptly provided to Legal Incident Responders, enabling formal takedown requests to be issued, or were shared directly with Australian and international law enforcement agencies. In multiple instances, this led to the disruption of exfiltration infrastructure, including the successful removal of data repositories where stolen information was being held.
However, even where takedowns have been effective, data is still published in the vast majority of cases where a ransom payment is not negotiated. This reinforces the reality that Threat Actors maintain multiple copies of exfiltrated data, often across different platforms or locations. This was clearly illustrated in recent law enforcement operations targeting LockBit, where data persisted despite claims by the ransomware group that it had been deleted.
Assume Compromise — Always
These findings underscore the importance of assuming data is compromised once exfiltrated, regardless of whether it appears to have been removed, and reinforce the value of timely legal engagement during the incident response process.

Ransom Payments
The Decline of Payouts in 2025
The 2024–25 financial year saw a significant decline in ransom payments, continuing a positive trend in organisational resilience. Out of 63 ransomware investigations conducted, a ransom was paid in only three cases, representing just 4.8% of engagements. This is a marked drop from the 13% payment rate observed in the 2023–24 financial year, indicating both a shift in incident response decisions and growing confidence in recovery strategies.
Several contributing factors have been identified. Firstly, many victim organisations had robust backup and recovery capabilities in place, which enabled them to restore operations without needing to negotiate with Threat Actors. Secondly, a number of organisations were targeted by sanctioned ransomware groups, which made payment legally impossible, regardless of their ability to recover. In other cases, organisations assessed the cost of data recovery, including rebuilding from non-encrypted systems, offsite data, or prior exports and found it to be more economical than paying for a decryption tool. Finally, a growing number of organisations are taking a principled stance, refusing to pay on moral grounds in an effort to disrupt the ransomware business model and avoid reinforcing its profitability.
In addition to the reduced frequency of payments, the average ransom paid also declined. This year, the average payment was approximately $77,000 USD, down from $115,000 USD the previous year.


Ransomware Themes
Third Party Compromise
A recurring theme in this year’s ransomware investigations was the compromise of environments through third-party access. These compromises often stemmed from a lack of visibility and control over how service providers and contractors were interacting with internal systems. In many cases, Threat Actors were able to gain initial access by exploiting weaknesses in third-party systems.
We observed several systemic issues across environments impacted by third-party compromise:
- Many accounts were assigned to third party IT providers, which had been assigned full administrator privileges.
- Access into the client environment was permitted via unmanaged devices, in essence allowing for connections to originate from any location as long as the credentials were valid.
- No MFA enforcement had been applied for external access. One instance found an IT MSP had enforced MFA for all client connections, however excluded their own account from this requirement.
- Limited visibility of how and when the third-party was expected to connect into the client network.
In many instances, external parties were being treated as trusted insiders, but without the same controls or oversight applied to internal staff.
In one case, an organisation had experienced a ransomware incident as a result of a third-party credential compromises. Following the incident, the third-party was offboarded and the project was close. Despite this, appropriate steps were still not followed to disable the access assigned to the third-party. It was subsequently found that the organisation took weeks to disable access following the cessation of the contract.
A broader contributing factor was the absence of structured identity and access management. Many organisations lacked a centralised register of third-party accounts, did not log activity associated with external users accessing internal systems, and relied on informal processes to manage onboarding and offboarding.
Lack of monitoring
One of the most consistent findings in Triskele Labs' ransomware investigations this year was the absence of action associated with responding to security alerts. In nearly every case involving unauthorised access to infrastructure, there were early indicators or alerts raised as part of the compromise. These alerts either went unnoticed, were misinterpreted, or were simply never seen.
We observed environments where Endpoint Detection and Response (EDR) tooling was deployed and functioning, yet the alerts it generated were:
- Mis-triaged or ignored by Managed Security Service Providers (MSSPs), Managed Service Providers (MSPs), or internal IT teams. In one instance, an external provider of a ransomware victim directly warned the organisation that their environment had been compromised by a ransomware Threat Actor. This warning was ignored, and the organisation was subsequently encrypted less than 24 hours later.
- Being forwarded to inboxes or ticket queues that were not being actively monitored, or were being flooded with alerts from all security and IT platforms that resulted in significant alerts being downed out by noise.
- Generated outside of business hours, with no arrangements in place for after-hours monitoring or response.
In some incidents, the security tooling in place was not fit for purpose. Legacy antivirus or basic antimalware solutions were still being relied upon in enterprise environments, despite well-known limitations in detecting modern attacker behaviours such as credential theft, lateral movement, and scripting activity. These products were easily disabled or bypassed by Threat Actors during the early stages of compromise.
While technology was technically present in many cases, the real issue was operational. Many victims lacked defined processes, ownership, or appropriate resourcing that allowed small issues to become major breaches.
Password Hygiene
Credential misuse and poor access control remain some of the most consistent themes observed during ransomware investigations. In far too many cases, initial access or privilege escalation was gained not through sophisticated actions but through basic oversights that centred around weak passwords, shared accounts, and the absence of appropriate password controls.
It was common to encounter spreadsheets full of credentials stored in shared drives, often unprotected and accessible to anyone with network access. We regularly saw variants of the same passwords reused widely across environments, including between user and administrator accounts and across both production and backup environments. These practices made lateral movement trivial for Threat Actors once they gained an initial foothold.
Many organisations had no formal process to offboard staff or disable expired accounts, leaving unused credentials lingering for months or years. In environments without identity management, oversight of administrator accounts was often not performed at all.
The cumulative effect of these practices has led to Threat Actor leveraging basic techniques, including manually searching through shared drives, in order to elevate privileged. threat landscape where attackers don’t need to be particularly sophisticated. While Triskele Labs has observed many organisations increasing their spending on cyber security controls, there are still weakness centred around the behaviour of users within environments.
Business Email Compromise (BEC) Investigations
Overview
Business Email Compromise (BEC) incidents represented 45% of all incidents handled by Triskele Labs in the 2024-25 financial year. Although the operational impact of BEC incidents is generally less severe than that of ransomware attacks, the financial consequences can be substantial, especially when payment direction fraud is involved.
These attacks responded to by Triskele Labs predominantly target victims using the Microsoft 365 (M365) suite of business productivity applications (I.E. Microsoft Outlook), reflecting its dominance as the primary platform for business communications in Australia and New Zealand.
Understanding Business Email Compromise
The vast majority of BEC incidents observed across investigations are performed by Threat Actors that are financially motivated.
- The most common outcome is payment redirection fraud, where attackers impersonate suppliers, executives, or staff to trick victims into transferring funds to attacker-controlled accounts.
- In some cases, the compromise is leveraged to scam downstream individuals or partner organisations, further amplifying the impact.
The impactful nature of financially motivated Threat Actors remained the primary driver of detection for BECs, which was most commonly detected as a result of:
- The business detecting attempted or successful payment redirection fraud conducted by the Threat Actor.
- The business is alerted to suspicious emails being sent by the Threat Actor to external parties, typically in the form of phishing emails that have been distributed in an attempt by the Threat Actor to extend their access to new victims.
BECs associated with solely information gathering objectives were rarely observed, in part due to the less impactful nature of these Threat Actors and the fact that they are less common amongst Australian small and medium businesses. Financially motivated Threat Actors continue to use techniques that result in the access and collection of information from mailbox users and the risk of this taking place as part of BECs remains, even when it is not the primary motivation of the Threat Actor.
Threat Actors are leveraging techniques designed to establish and exploit trust. Phishing campaigns typically sent once the Threat Actor has exhausted opportunities to complete payment redirection fraud within a compromised impacts, are most commonly observed issuing out phishing emails to known contacts of the compromised mailbox.
Instead of sending a malicious attachment or direction users to a suspicious URL, it is becoming increasingly common for Threat Actor to create documents within the legitimate file sharing platforms of the compromised account (I.E. SharePoint, OneDrive, Dropbox) and sharing access to the document. Receiving a link to a document hosted within a legitimate sharing location, from a known contact, is resulting in Threat Actors furthering their access to new victims.
Role of Forensics
Digital Forensics and Incident Response (DFIR) investigations are conducted with extensive experience and knowledge of the investigative process. DFIR acts as an external, trusted party focused on delivering unbiased, fact-based insights critical to understanding cyber incidents. While internal IT staff or external IT Managed Service Providers provide valuable support, often investigations do not capture the nuanced details and techniques that an investigation requires.
The objectives of a DFIR BEC investigation typically are to:
- Confirm that there had been unauthorised access to mailbox(es).
- Identify how the Threat Actor was able to gain initial access to the environment.
- Identify what actions were performed by the Threat Actor whilst they had access.
- Identify whether Personally Identifiable Information (PII) or Protected Health Information (PHI) had been accessed by the Threat Actor.
- Ensure that the Threat Actor has been purged from the environment.
- Provide guidance with the remediation and recovery activities.
- Provide recommendations to strengthen the cyber security posture post incident.
Traditional investigation methods are increasingly falling short, particularly given the growing complexity of Business Email Compromise BEC techniques. Notably, Threat Actors are now employing persistence mechanisms not observed in previous financial years, allowing them to maintain access even after standard containment and investigative measures have been applied.
Stages of a Business Email Compromise
Initial Access
Over the past financial year, Threat Actors have increasingly leveraged legitimate infrastructure, such as free hosting platforms, to host redirection and landing pages. These pages are often customised to match the branding of the compromised organisation, including their logo and business name. Because they are hosted on legitimate services and typically contain only a secondary link (rather than a direct credential harvester), they frequently bypass email filtering controls.
The delivery of phishing campaigns is widely being facilitated through legitimate services such as SharePoint, DropBox and MailChimp. Files that contain a link to a credential harvester will be uploaded to the legitimate platform, where the Threat Actor will subsequently leverage the platform’s share functionality to distribute access to the file to victims. Some platforms also include the ability to schedule follow-up reminders, which can further continue the phishing emails delivery.
Threat Actors have been observed applying MFA to external SaaS solutions (I.E. DropBox, MailChimp) in order to prevent the legitimate account holders from regain access to the account.
QR code phishing (or 'quishing') remains in use, although it is currently less prevalent than the newer delivery methods described above.
Evidence Sources
As of 1 March 2025, Microsoft stopped writing audit log data directly to mailboxes. From this date forward, activity attributed to actions performed within an account is only captured within Unified Audit Log (UAL), under the condition that UAL is enabled. For Microsoft 365 tenancies created after 2021, the UAL is enabled by default. However, tenants created in 2021 or earlier will not have this enabled by default.
To check whether UAL is enabled, a privileged account holder can visit https://purview.microsoft.com and navigate to the ‘Audit’ section. If the UAL is not enabled, a blue banner will appear prompting you to turn it on. Enabling it may take several minutes to take effect.
Alternatively, UAL status can be verified using PowerShell:
- Run Connect-ExchangeOnline to authenticate.
- Enter Get-AdminAuditLogConfig to retrieve the audit log configuration.
- Review the fields UnifiedAuditLogIngestionEnabled and UnifiedAuditLogFirstOptInDate to determine if the UAL is active and when it was enabled.
- If not enabled, you can enable it by running: Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
Data Exfiltration
A critical part of a Business Email Compromise (BEC) investigation is determining whether mailbox synchronisation has occurred, as this process creates a local offline copy of the mailbox. While synchronisation is designed to improve productivity by allowing users to access emails even without internet connectivity. This functionality has also introduced risk during mailbox compromises as Threat Actors can obtain a complete copy of any mailbox contents.
Delegate access is another key consideration. Within many organisations, it is common for users to be granted access to shared mailboxes or other employees’ mailboxes for operational purposes. If a compromised user account has such access, the impact of the incident can quickly expand beyond a single mailbox, increasing the overall risk and complexity of the investigation.
Email clients like Microsoft Outlook automatically create an Offline Outlook Data File (OST) when a user signs in, storing emails, calendar events and contacts on the local device. This means that a Threat Actor who signs into a compromised mailbox using the Outlook desktop application can generate a full local copy of the mailbox—accessible even after containment measures are applied.
Third-party applications like eM Client provide similar functionality and are sometimes used by Threat Actors to send and receive emails from compromised accounts. eM Client supports full mailbox synchronisation, with the default configuration set to synchronise all messages excluding attachments. However, it can be adjusted to download full mailbox contents, including attachments, to the local device.
Threat Actors may also leverage legitimate cloud backup tools such as PerfectData Software to exfiltrate mailbox data. PerfectData enables complete mailbox backups from various services, including Microsoft 365 and IMAP. When used maliciously, this allows a Threat Actor to extract an entire mailbox during the window of compromise, often before any containment or recovery actions have been taken.
Persistence
One of the more advanced techniques observed in Business Email Compromise (BEC) cases for the first time this financial year was the use of Azure App Registrations to maintain persistence within Microsoft 365 environments. This technique allows Threat Actors to create an authorised application that can access mailbox data and other M365 resources via Graph API, even after credentials are reset or MFA is enforced. It is particularly effective in scenarios where traditional containment measures (I.E. password resets) are applied without a thorough investigation. In these cases, the Threat Actor can silently retain access to the environment.
In 28% of BEC cases investigated across the financial year, Triskele Labs identified some form of persistence mechanism being leveraged. Azure App Registrations were a notable trend, closely mirroring the capabilities of offensive tooling like GraphRunner, which is designed to abuse Graph API permissions. Other persistence techniques included the use of Temporary Access Passes (TAPs), the creation of new Microsoft 365 accounts, and the reactivation or password reset of dormant or inactive accounts.
These findings reinforce the need for a deeper investigative approach when responding to BEC incidents. If containment is completed without identifying and removing the mechanisms Threat Actors have established for persistence, organisations risk ongoing unauthorised access and further compromise.
Payment Redirection Fraud
Once a mailbox has been compromised, the primary motivation of the Threat Actor is typically to conduct payment redirection fraud. In many cases, the compromised organisation itself facilitates the attempt by providing the attacker with access to email conversations, invoice templates, and contact details for clients. Threat Actors use this access to impersonate the organisation in an attempt to deceive clients into transferring funds to attacker-controlled bank accounts.
However, it's increasingly common for the compromised organisation to become the victim of the fraud itself. Threat Actors are frequently registering lookalike domains to impersonate trusted suppliers or service providers, allowing them to target accounts payable teams within a legitimate business. Many organisations are drawn in through convincing emails that appear to originate from a legitimate source, with only subtle indicators of fraud. This reinforces the importance of human controls that include validating bank detail changes through a known phone number, using multi-party approval workflows for financial transactions, and training staff to identify red flags. While technical controls can reduce risk, it is often these manual validation steps that prevent fraudulent payments from being made.
Payment redirection fraud was attempted in 27% of Business Email Compromise (BEC) cases investigated by Triskele Labs over the financial year. Of those cases, Threat Actors successfully achieved their objective in 40% of attempts, highlighting the effectiveness of this tactic when detection and human validation controls fail.
On average, successful attempts resulted in the redirection of $107,927 which represented the significant financial impact that can arise from a single compromised mailbox or supplier impersonation.
Detection
Most BEC incidents are first identified in one of two ways:
- Receipt of an external notification following phishing emails sent from the compromised account; or
- An internal discovery due to delayed payments or financial discrepancies.
The delayed and reactive nature of these detection methods means Threat Actors are often able to operate within the environment unnoticed for an extended period. Across cases investigated by Triskele Labs, the average dwell time before detection was 32 days (down from 41 days in the previous financial year), with most incidents only identified once the attacker took an action that caused visible impact.
Payment Redirection Fraud
Once a mailbox has been compromised, the primary motivation of the Threat Actor is typically to conduct payment redirection fraud. In many cases, the compromised organisation itself facilitates the attempt by providing the attacker with access to email conversations, invoice templates, and contact details for clients. Threat Actors use this access to impersonate the organisation in an attempt to deceive clients into transferring funds to attacker-controlled bank accounts.
However, it's increasingly common for the compromised organisation to become the victim of the fraud itself. Threat Actors are frequently registering lookalike domains to impersonate trusted suppliers or service providers, allowing them to target accounts payable teams within a legitimate business. Many organisations are drawn in through convincing emails that appear to originate from a legitimate source, with only subtle indicators of fraud. This reinforces the importance of human controls that include validating bank detail changes through a known phone number, using multi-party approval workflows for financial transactions, and training staff to identify red flags. While technical controls can reduce risk, it is often these manual validation steps that prevent fraudulent payments from being made.
Payment redirection fraud was attempted in 27% of Business Email Compromise (BEC) cases investigated by Triskele Labs over the financial year. Of those cases, Threat Actors successfully achieved their objective in 40% of attempts, highlighting the effectiveness of this tactic when detection and human validation controls fail. On average, successful attempts resulted in the redirection of $107,927 which represented the significant financial impact that can arise from a single compromised mailbox or supplier impersonation.
Detection
MostBEC incidents are first identified in one of two ways:
- Receipt of an external notification following phishing emails sent from the compromised account; or
- An internal discovery due to delayed payments or financial discrepancies.
The delayed and reactive nature of these detection methods means Threat Actors are often able to operate within the environment unnoticed for an extended period.Across cases investigated by Triskele Labs, the average dwell time before detection was 32 days (down from 41 days in the previous financial year), with most incidents only identified once the attacker took an action that caused visible impact.
PaymentRedirection Fraud
Once a mailbox has been compromised, the primary motivation of the Threat Actor is typically to conduct payment redirection fraud. In many cases, the compromised organisation itself facilitates the attempt by providing the attacker with access to email conversations, invoice templates, and contact details for clients. Threat Actors use this access to impersonate the organisation in an attempt to deceive clients into transferring funds to attacker-controlled bank accounts.
However, it's increasingly common for the compromised organisation to become the victim of the fraud itself. Threat Actors are frequently registering lookalike domains to impersonate trusted suppliers or service providers, allowing them to target accounts payable teams within a legitimate business. Many organisations are drawn in through convincing emails that appear to originate from a legitimate source, with only subtle indicators of fraud. This reinforces the importance of human controls that include validating bank detail changes through a known phone number, using multi-party approval workflows for financial transactions, and training staff to identify red flags.While technical controls can reduce risk, it is often these manual validation steps that prevent fraudulent payments from being made.
Payment redirection fraud was attempted in 27% of Business Email Compromise (BEC) cases investigated by Triskele Labs over the financial year. Of those cases, ThreatActors successfully achieved their objective in 40% of attempts, highlighting the effectiveness of this tactic when detection and human validation controls fail.
On average, successful attempts resulted in the redirection of $107,927 which represented the significant financial impact that can arise from a single compromised mailbox or supplier impersonation.
BEC Themes
Session Token Theft
While the uptake of Multifactor Authentication (MFA) continues slowly across Australia, Across Australia and New Zealand, many businesses are implementing MFA as there it has been a common belief that MFA will mitigate the risk of credential compromise. Unfortunately, Threat Actors are continuing to embed techniques within their technology to bypass these MFA controls, particularly within the Microsoft 365 platform due to it’s prevalence of use across the industry.
Session token theft is a form of Adversary-in-the-Middle (AitM) attack whereby a Threat Actor will develop a credential harvester that impersonates the Microsoft 365 authentication portal. As a victim enters their legitimate username, password and MFA token within the credential harvester, the information is used to legitimate authenticate into Microsoft 365 in order to collect an authorised session token.
Many users are on the lookout for suspicious emails or poorly coded authentication portals, however the technologies in use by Threat Actors are bypassing these perceptions of the public and resulting in successful email compromises.
In one instance across FY25, the leader of a small business has been championing cyber awareness within their organisation and led a 12 month education and training program amongst staff. At the end of this program, the leader fell victim to a phishing campaign that leveraged common techniques. Information provided by the leader found that these common techniques had not been included as part of the provided training.
The techniques used by Threat Actors are streamlined and being used frequently to conduct attacks which can be shared with staff easily to increase awareness and build the cyber resilience of organisations.
Mobile Devices
While the convenience offered by accessing emails from your phone is seen as a positive for many business leaders, it also introduces an additional risk when it comes of the proliferation of BECs and payment redirection fraud.
- Many common email applications designed for mobile devices will only show the senders email name, not the full email address. This has been a contributing factor in many BECs across FY25, where the recipient of the email does not identify that a Threat Actor is impersonating the email address of an external contact.
- It is common for staff to use personal mobile devices which are not managed by the organisation. Actions associated with interactions with phishing emails or malicious attachments are not detected by the organisation’s security tooling.
- Some Threat Actor continue to leverage QR codes as a mechanism to deliver credential harvesters, which are designed to initiate activity from mobile devices, instead of managed laptops and endpoints.
Excessive Permissions
Particularly common across small businesses, Triskele Labs has found that many businesses and user accounts are being assigned excessive (or top level) administrative privileges within email environments.
Larger organisations have mature processes in place that necessitate the implementation of Identity and Access Management, Principles of Least Privilege and dedicated Service Accounts for administrative users. For smaller businesses, it is not uncommon for leaders or office administrators to be assigned administrative permissions that are commonly being exploited by Threat Actors.
In one instance recently responded to by Triskele Labs, an IT user was assigned temporary top level privileges within their Microsoft 365 tenancy in order to complete an upgrade project. During these period of elevated access, the user’s account was compromised by a Threat Actor. Leveraging the top-level privileges, the Threat Actor commandeered the entire Microsoft 365 and Azure Cloud tenancy of the business and locked legitimate business users out of the environment entirely.
Many users assigned top-level privileges (I.E. Microsoft 365’s Global Administrator role) do not require the full use to the assigned permissions and would benefit from being assigned a role with fewer account privileges.
Even for standard user accounts, there are privileges commonly assigned that are being exploited by Threat Actors to enable the rapid access and collection of information from the mailbox user. Microsoft 365 allows for users to authenticate to third-party applications in order to interact with their accounts in different ways; Threat Actors are frequently exploiting this permission and authenticating to applications designed to collect copies of mailboxes, extract information from mailboxes or issue mass phishing campaigns from mailboxes.
Key BEC Controls
There are some common controls Triskele Labs recommends to mitigate the likelihood and impact of BECs affecting organisations:
- Enforce Multi-Factor Authentication to protect again unsophisticated attack methods (I.E. credential stuffing).
- Implement policies to restrict access to resources from outside of expected locations or services (I.E. Geoblocking policies, third-party applications, unauthorised devices)
- Segregate administrative access to platforms to dedicated non-user accounts.
- Assess the opportunities to implement session token protection controls.
- Implement 24x7 monitoring in order to detect unusual sign-in activities.
- Govern how third-party administrative access is being assigned and monitored.
Emerging Risks
Lack of Encryption
The emergence of ransomware Threat Actors that don’t encrypt data. Throughout FY25, Triskele Labs identified two (2) Threat Actors that obtained sufficient access to internal systems to allow for encryption to be deployed, however the Threat Actor was observed actively choosing not to encrypt victim environments:
- One Threat Actor made assertions of their leak site that while they did compromise and extort victims across all industry verticals, they did not encrypt the environments of healthcare providing organisations. Triskele Labs noted that this Threat Actor followed this rule on one (1) occasions, whilst breaking in earlier in the year for other healthcare providing victims.
- A new Threat Group emerged in FY25 that does not seek to encrypt victims. Instead of encrypting systems and making them unavailable, this Threat Actor solely exfiltrates data and relies on organisations seeking to pay in order to prevent the data from being published.
Further to this, examples were identified of Threat Actors, notably KillSec3, conducting exfiltration attacks against publicly accessible data stores and vulnerable File Transfer Protocol (FPT) servers. During these attacks, the Threat Actor sought to exfiltrate unprotected data from these locations and publish the data on their Dark Web leak site. In manage instances the organisation was unaware that the incident had occurred until the name of the organisation was listed on a Dark Web leak site.
With many organisations not applying appropriate controls to personal, sensitive or health information, Threat Actors are presented with less barriers to exfiltrate data than they are to encrypt systems.
Key Controls:
- Network restrictions to prevent open internet access from infrastructure.
- Adoption of Data Loss Prevention (DLP) controls.
- Strong Identify and Access Management (IAM) controls restricting unnecessary access. permissions within the environment.
- Data encryption at risk.
- Secure configuration and management of file storage and file transfer infrastructure.
Endpoint Compromise
Throughout FY25, Triskele Labs responded to multiple cyber incidents that originated from endpoint compromises.
In one example, Triskele Labs successfully attributed a ransomware attack to the deployment of credential stealing software that was deployed to an unmanaged device.
Across FY24 and FY25, Triskele Labs observed ransomware Threat Actors exploiting weaknesses within external access controls (I.E. lack of MFA configured for remote access) in order to establish access within victim environments. Once environments were compromised, Threat Actors would remain connected to server infrastructure in order to complete their attacks.
In order to allow staff to fulfill the requirements of their role, it is not uncommon for Endpoints to be provisioned with less restrictive access controls. Threat Actors were observed leveraged user endpoints across FY25 to exfiltrate data and bypass administrative access controls.
Key Controls:
- Restrict unmanaged devices from directly connecting to enterprise resources (I.E. BYOD).
- Deploy Enterprise Password Vaults to encourage good password hygiene and prevent passwords from being stored within insecure repositories like web browsers.
- Provision alternative access methods into environments for third parties (I.E. Managed RMM, Citrix Workspaces)
- Strength segregation between server infrastructure and user endpoints.
Unreported Incidents
Within FY25, three ransomware incidents were investigated by Triskele Labs where external IT Managed Service Providers did not inform their customers of significant cyber incidents.
- Three MSPs did not tell customers that their environment had been victim to a ransomware incident, instead advising customers that their environment had experienced an IT disruption.
Key contributing factors observed across these cases included:
- Security alerts were generated but not reviewed or escalated, despite opportunities to detect and contain the threat early.
- Basic preventative or detective controls (e.g. MFA, endpoint detection, segmentation) were missing or inconsistently implemented across the environments.
- Agreements between the client and provider often lacked clarity around roles and responsibilities during a security incident. In some cases, newly formed relationships or commercial pressures appeared to influence disclosure decisions.
These incidents highlight a persistent and growing risk where third-party IT providers fail to meet their obligations during cyber events. The absence of clear contractual responsibilities and inconsistently applied security controls increases the likelihood of cyber incidents occurring and continues to leave companies exposed.
Importantly, this trend aligns with a broader shift in appetite from both insurers and victim organisations to pursue financial recovery or compensation from third parties whose failures contributed to an incident. With changes to the Australian Privacy Act expanding enforcement powers and introducing higher penalties for serious or repeated interferences with privacy, it is likely that FY26 will see increased legal and financial scrutiny of external service providers involved in cyber events.
Organisations are more frequently assessing the contractual, operational, and legal accountability of IT vendors post-incident, particularly where early intervention could have mitigated or prevented harm.
Key Controls:
- Ensure service agreements clearly require third parties to report security incidents within defined timeframes and cooperate during investigations.
- Implement shared visibility into critical security alerts so clients retain awareness of detections within the environment.
- Seek the support of an external party in order to establish whether the controls implemented by an MSP are appropriate.
Conclusion
The 2024–25 financial year highlighted a clear shift in the scale and consistency of cyber incidents impacting organisations across Australia and New Zealand. From endless BEC campaigns where phishing emails are being distributed to further the access of a Threat Actor, to highly disruptive ransomware attacks, Threat Actors demonstrated their ability to evade detection and exploit weaknesses within organisations in order to achieve their objectives. These incidents reinforce the need for proactive, not reactive, security strategies.
Culture, Awareness and Leadership Accountability
The most resilient organisations in FY26 will be those that treat cybersecurity as a shared responsibility. Security is not just an IT issue. Staff at all levels need to understand their role in preventing and responding to threats. Awareness programs need to go beyond basic phishing simulations and focus on real-world techniques used by attackers, including credential theft and social engineering.
Leadership also plays a critical role. Boards and senior executives must ensure that cybersecurity is prioritised, appropriately resourced, and governed. A lack of engagement at the top has been a common factor in many of the most damaging incidents Triskele Labs responded to. Cyber risk is now a core business risk.
Governance, Resilience and Recovery Planning
Many of the incidents Triskele Labs investigated during the year were preventable. Controls were often partially implemented, misconfigured, or poorly monitored. In some cases, legacy systems or third-party access created hidden risk due to weak governance and oversight.
Resilience is not just about stopping attacks. It also means being able to detect and respond to threats at any time. Backups should be tested regularly. Business continuity plans need to be updated to reflect current threats and realistic recovery timelines. Proactive security operations and well-defined response processes are essential.
Implementation, Integration and Monitoring
Core technical controls like MFA, endpoint protection and data loss prevention remain critical. However, having tools in place is not enough. They must be properly configured, monitored, and integrated with operational processes. Misconfigurations and gaps in visibility were key factors in many incidents.
In 2024–25, Threat Actors consistently exploited these weaknesses to gain access, move through networks undetected, and deploy ransomware or exfiltrate sensitive data. A layered and well-integrated technology stack is vital for early detection and effective response.




